% Introduction to Reverse Engineering
% Stefan Friese
% 02 November, 2023
---
# Topics
* Effective Reverse Engineering
* Reversing with Ghidra
---
## How Do You Reverse
Reverse Engineering demands a lot of knowledge in multiple fields.
**Some topics are**
* Assembly Language
* ANSI C
* Other Languages
* Syscalls
* Cryptography
---
How do you reverse engineer without knowing little about these topics?
---
## Reversing is Work
Work is a product of power by time.
`P` is your power to solve an issue.
`W = P x t`
The smarter you tackle work, the less time you need to solve an issue.
---
## Knowledge is a Map
You conventiently drive around the city using the underground.
That's how you get to know the main spots of the city.
 ---
## Knowledge is a Map
Invest some time and explore deeper on foot.
That's how you get to know the back alleys.
---
## Knowledge is a Map
Invest some time and explore deeper on foot.
That's how you get to know the back alleys.
 ---
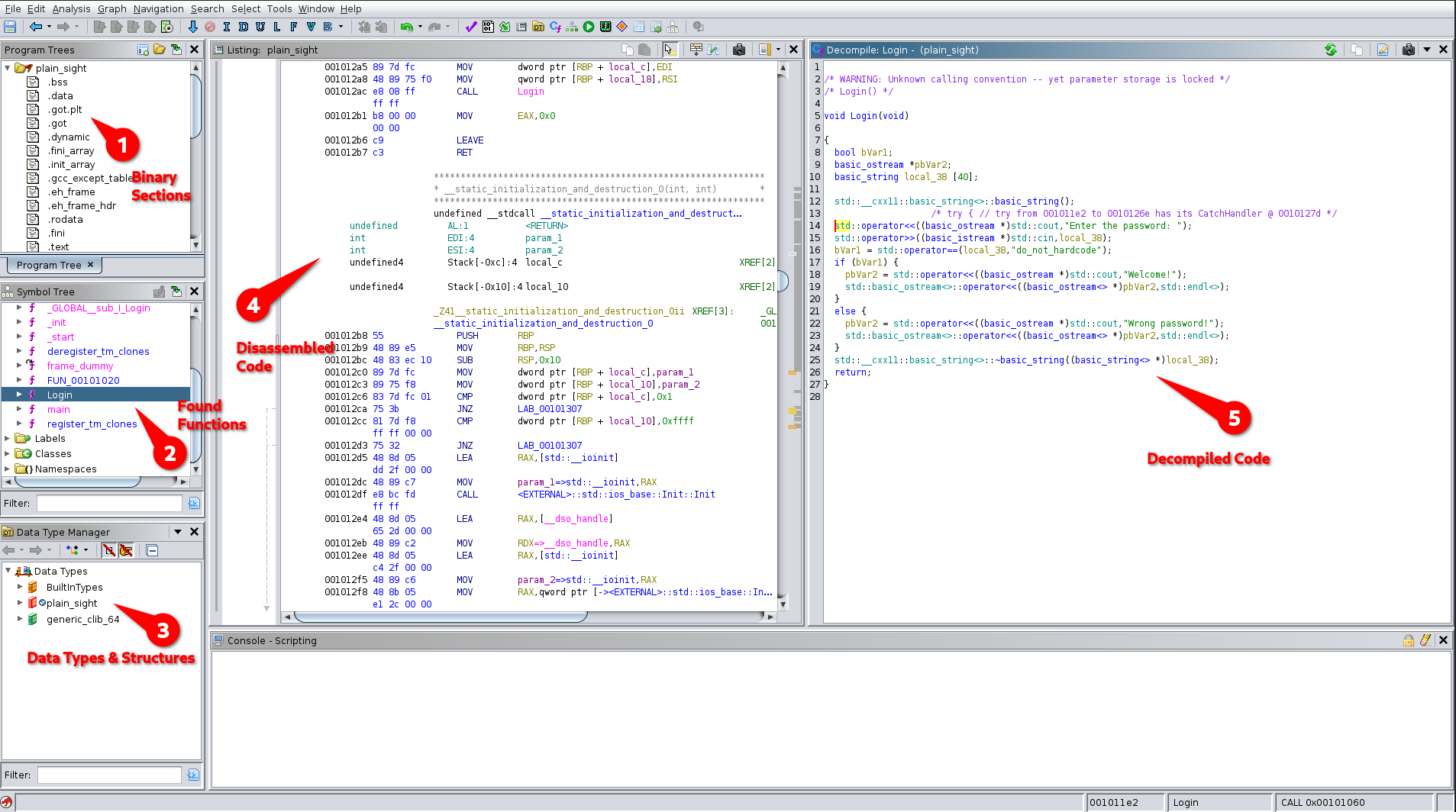
# Ghidra -- an Overview
---
---
## Watch Out for Low Hanging Fruits
---
* Data Segment
* Names of Functions
* Conditions & Comparisons
* Strings: Usernames, Passwords
* URLs, IP & Port Numbers
**Do not try to understand the whole code at once, it will only drive you mad.**
---
### Data Segments

---
### Name of Functions

---
### Conditions & Comparisions
---
# Ghidra -- an Overview
---

---
## Watch Out for Low Hanging Fruits
---
* Data Segment
* Names of Functions
* Conditions & Comparisons
* Strings: Usernames, Passwords
* URLs, IP & Port Numbers
**Do not try to understand the whole code at once, it will only drive you mad.**
---
### Data Segments

---
### Name of Functions

---
### Conditions & Comparisions
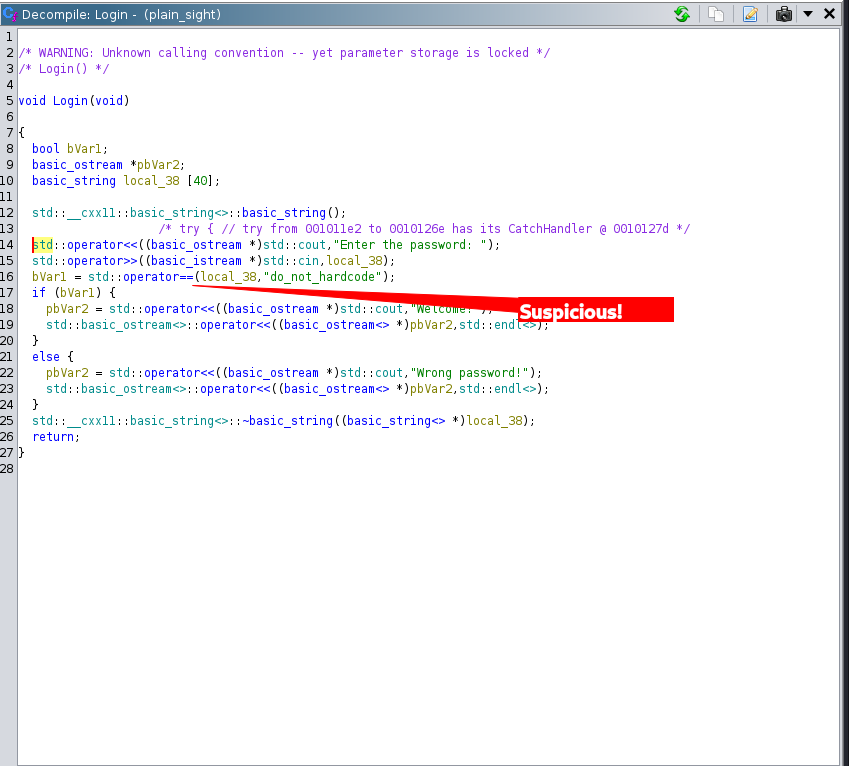 Input is compared to a hard coded string
---
### Function Graph
Input is compared to a hard coded string
---
### Function Graph
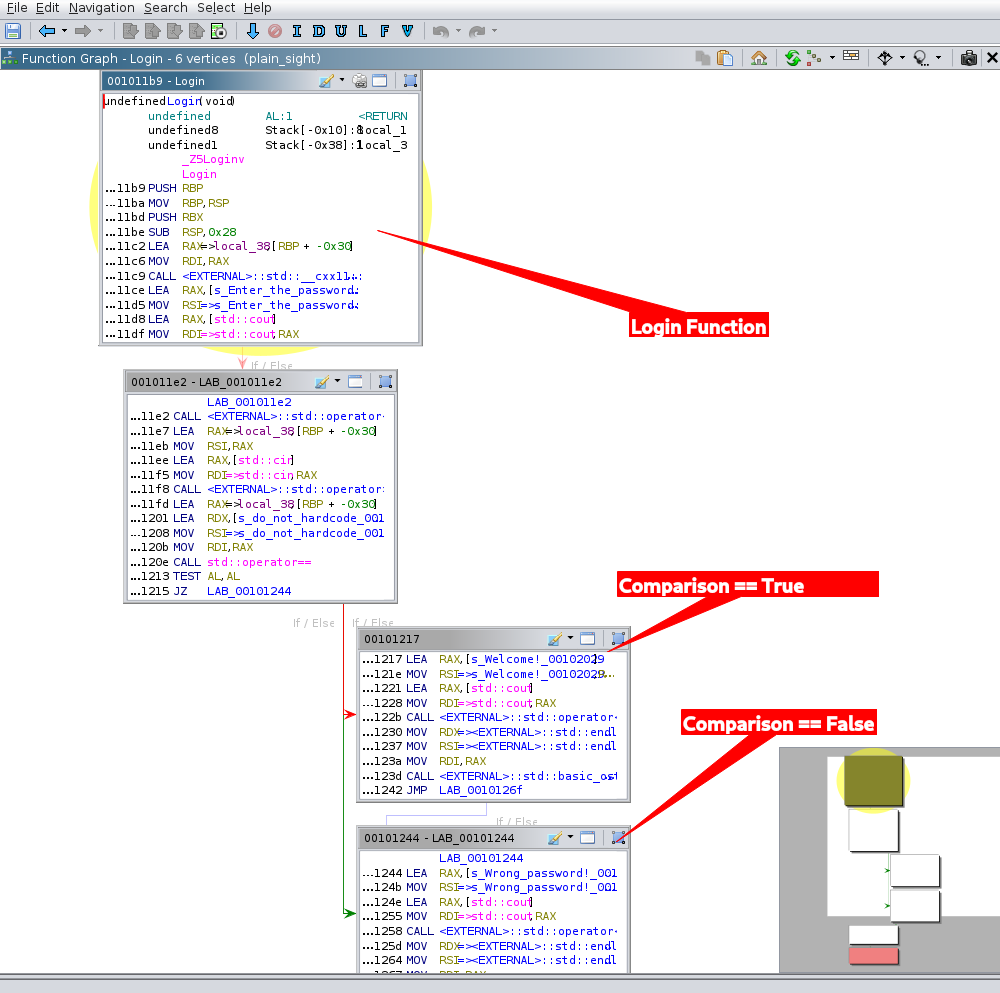 Take a look at the flow graph of functions
---
### Strings
Take a look at the flow graph of functions
---
### Strings
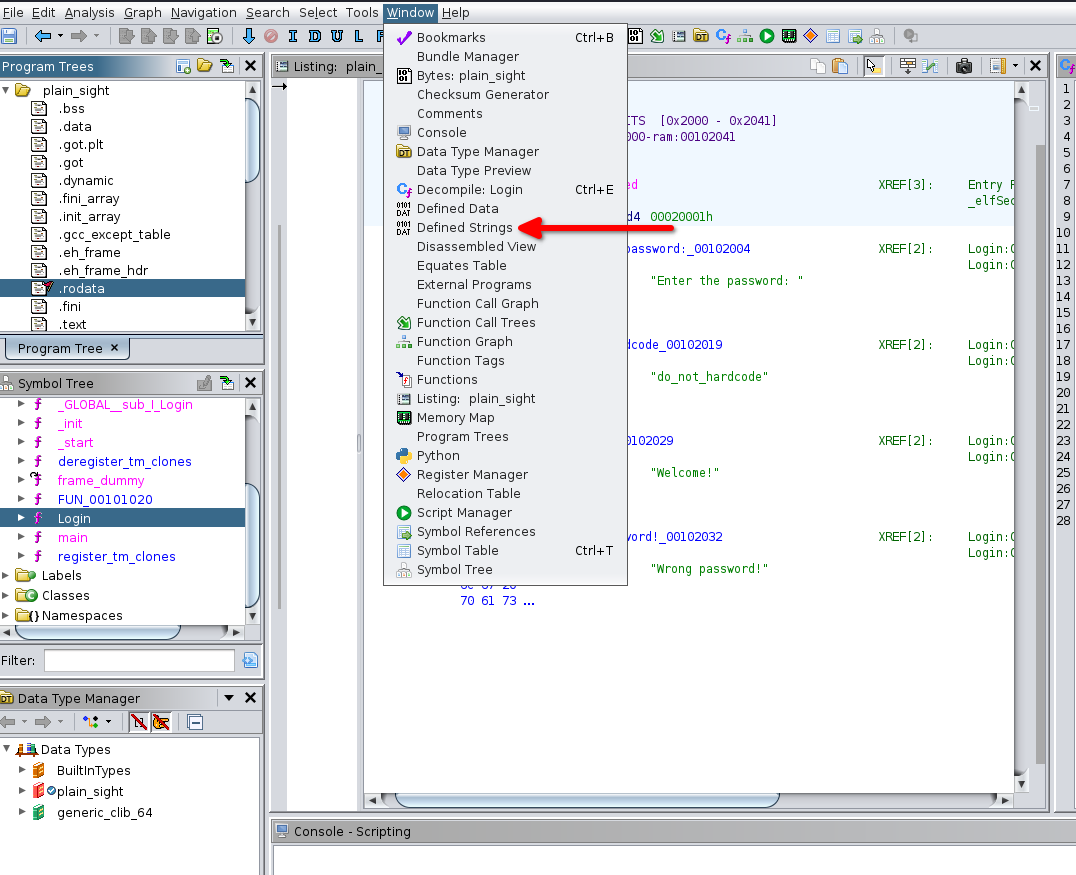 Strings can not only be located in data but also in other code segments, sometimes obfuscated
---
### Strings

---
### Do It Yourselves!
* [Download Ghidra](https://ghidra-sre.org/)
* [Download binaries at crackmes.one](https://crackmes.one)
* [Find more binaries on hackthebox](https://hackthebox.eu)
* [Or Find even more on tryhackme](https://tryhackme.com)
* Download firmware of your favorite IoT appliances
---
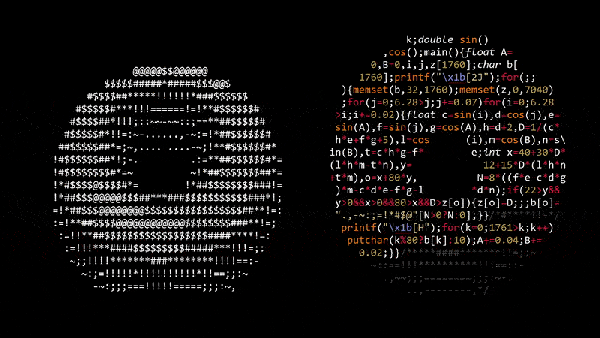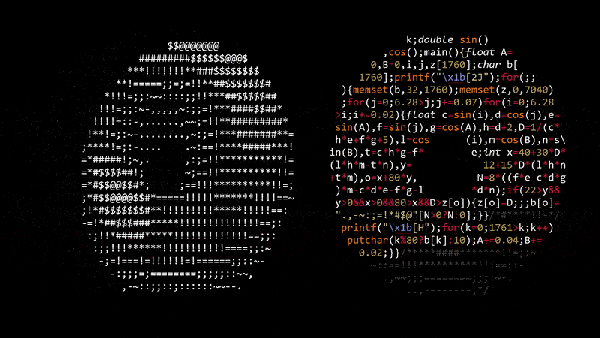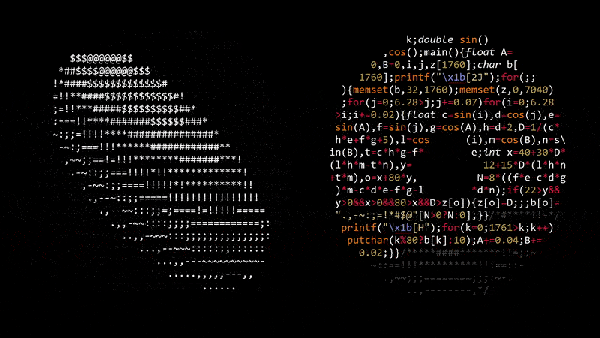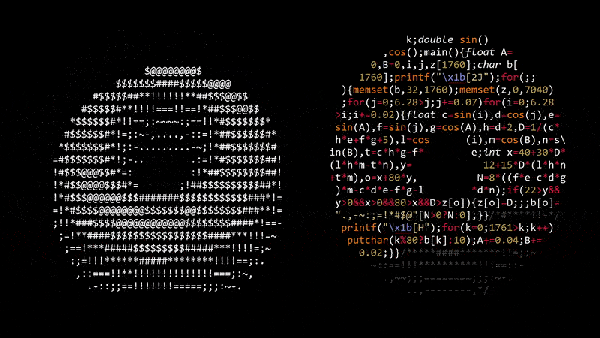
## A Word On Binary Obfuscation
Software Obfuscation was born in 1984 at the [International Obfuscated C Code Contest](https://ioccc.org/)
Strings can not only be located in data but also in other code segments, sometimes obfuscated
---
### Strings

---
### Do It Yourselves!
* [Download Ghidra](https://ghidra-sre.org/)
* [Download binaries at crackmes.one](https://crackmes.one)
* [Find more binaries on hackthebox](https://hackthebox.eu)
* [Or Find even more on tryhackme](https://tryhackme.com)
* Download firmware of your favorite IoT appliances
---
## A Word On Binary Obfuscation
Software Obfuscation was born in 1984 at the [International Obfuscated C Code Contest](https://ioccc.org/)
 ---
### What Exactly might be Obfuscated in Your Code?
[Layered obfuscation: a taxonomy of software obfuscation techniques for layered security by Hui Xu et. al](https://cybersecurity.springeropen.com/track/pdf/10.1186/s42400-020-00049-3.pdf)
* Code Element Layers
* Layout
* Controls
* Data
* Methods
* Classes
* Component
* Library Calls
* Used Resources
* Application Layer
* DRM System
* Neural Networks
---
## Techniques of Obfuscation
---
### Splitting & Merging of Strings
```sh
a = "BABE"
b = "CAFFEE"
f"{b}{a}"
```
[String Deobfuscation with FLOSS](https://github.com/mandiant/flare-floss/)
---
## Packing
```sh
ooooo ooo ooooooooo. ooooooo ooooo
`888' `8' `888 `Y88. `8888 d8'
888 8 888 .d88' Y888..8P
888 8 888ooo88P' `8888'
888 8 888 .8PY888.
`88. .8' 888 d8' `888b
`YbodP' o888o o888o o88888o
```
[UPX Packer/Unpacker](https://upx.github.io/)
---
### Mangling
---
### What Exactly might be Obfuscated in Your Code?
[Layered obfuscation: a taxonomy of software obfuscation techniques for layered security by Hui Xu et. al](https://cybersecurity.springeropen.com/track/pdf/10.1186/s42400-020-00049-3.pdf)
* Code Element Layers
* Layout
* Controls
* Data
* Methods
* Classes
* Component
* Library Calls
* Used Resources
* Application Layer
* DRM System
* Neural Networks
---
## Techniques of Obfuscation
---
### Splitting & Merging of Strings
```sh
a = "BABE"
b = "CAFFEE"
f"{b}{a}"
```
[String Deobfuscation with FLOSS](https://github.com/mandiant/flare-floss/)
---
## Packing
```sh
ooooo ooo ooooooooo. ooooooo ooooo
`888' `8' `888 `Y88. `8888 d8'
888 8 888 .d88' Y888..8P
888 8 888ooo88P' `8888'
888 8 888 .8PY888.
`88. .8' 888 d8' `888b
`YbodP' o888o o888o o88888o
```
[UPX Packer/Unpacker](https://upx.github.io/)
---
### Mangling
c++filt
_ZNSt7__cxx1114collate_bynameIcEC2ERKNS_12basic_stringIcSt11char_traitsIcESaIcEEEm
std::__cxx11::collate_byname::collate_byname(std::__cxx11::basic_string, std::allocator > const&, unsigned long)
---
### Code Elements
* Adding Unnecessary Instructions
* Changing Control Flows
* Protecting Data
 ---
### Deobfuscation Tools
* DotNet
* [de4dot Deobfuscator and Unpacker](https://github.com/de4dot/de4dot)
* [dnSpy Debugger and Assembly Editor](https://github.com/dnSpy/dnSpy)
* [ILSpy Decompiler instead of Ghidra](https://github.com/icsharpcode/ILSpy)
---
### Deobfuscation Tools
* DotNet
* [de4dot Deobfuscator and Unpacker](https://github.com/de4dot/de4dot)
* [dnSpy Debugger and Assembly Editor](https://github.com/dnSpy/dnSpy)
* [ILSpy Decompiler instead of Ghidra](https://github.com/icsharpcode/ILSpy)
 ---
## Knowledge is a Map
Invest some time and explore deeper on foot.
That's how you get to know the back alleys.
---
## Knowledge is a Map
Invest some time and explore deeper on foot.
That's how you get to know the back alleys.
 ---
# Ghidra -- an Overview
---

---
## Watch Out for Low Hanging Fruits
---
* Data Segment
* Names of Functions
* Conditions & Comparisons
* Strings: Usernames, Passwords
* URLs, IP & Port Numbers
**Do not try to understand the whole code at once, it will only drive you mad.**
---
### Data Segments

---
### Name of Functions

---
### Conditions & Comparisions
---
# Ghidra -- an Overview
---

---
## Watch Out for Low Hanging Fruits
---
* Data Segment
* Names of Functions
* Conditions & Comparisons
* Strings: Usernames, Passwords
* URLs, IP & Port Numbers
**Do not try to understand the whole code at once, it will only drive you mad.**
---
### Data Segments

---
### Name of Functions

---
### Conditions & Comparisions
 Input is compared to a hard coded string
---
### Function Graph
Input is compared to a hard coded string
---
### Function Graph
 Take a look at the flow graph of functions
---
### Strings
Take a look at the flow graph of functions
---
### Strings
 Strings can not only be located in data but also in other code segments, sometimes obfuscated
---
### Strings

---
### Do It Yourselves!
* [Download Ghidra](https://ghidra-sre.org/)
* [Download binaries at crackmes.one](https://crackmes.one)
* [Find more binaries on hackthebox](https://hackthebox.eu)
* [Or Find even more on tryhackme](https://tryhackme.com)
* Download firmware of your favorite IoT appliances
---
## A Word On Binary Obfuscation
Software Obfuscation was born in 1984 at the [International Obfuscated C Code Contest](https://ioccc.org/)
Strings can not only be located in data but also in other code segments, sometimes obfuscated
---
### Strings

---
### Do It Yourselves!
* [Download Ghidra](https://ghidra-sre.org/)
* [Download binaries at crackmes.one](https://crackmes.one)
* [Find more binaries on hackthebox](https://hackthebox.eu)
* [Or Find even more on tryhackme](https://tryhackme.com)
* Download firmware of your favorite IoT appliances
---
## A Word On Binary Obfuscation
Software Obfuscation was born in 1984 at the [International Obfuscated C Code Contest](https://ioccc.org/)
 ---
### What Exactly might be Obfuscated in Your Code?
---
### What Exactly might be Obfuscated in Your Code?
 ---
### Deobfuscation Tools
* DotNet
* [de4dot Deobfuscator and Unpacker](https://github.com/de4dot/de4dot)
* [dnSpy Debugger and Assembly Editor](https://github.com/dnSpy/dnSpy)
* [ILSpy Decompiler instead of Ghidra](https://github.com/icsharpcode/ILSpy)
---
### Deobfuscation Tools
* DotNet
* [de4dot Deobfuscator and Unpacker](https://github.com/de4dot/de4dot)
* [dnSpy Debugger and Assembly Editor](https://github.com/dnSpy/dnSpy)
* [ILSpy Decompiler instead of Ghidra](https://github.com/icsharpcode/ILSpy)