# AWS Enumeration
## Regions
[A list of services by region](https://aws.amazon.com/about-aws/global-infrastructure/regional-product-services/) is maintained by AWS
There are global and regional services.
Watch out for the global and regional __Security Token Service__ (STS) which
provides temporary access to third party identities, since regional STS are
also valid in other regions. Global STS are only valid in default regions.
In aws cli, [Regions](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-regions-availability-zones.html#concepts-available-segions) go the cli argument `--region`
## Identity Access Management (IAM)
Permissions are granted directly through IAM identities (IAM Principals) inside
an AWS account or indirectly through
groups and roles the principal (user or service) has joined.
```sh
aws iam list-users
```
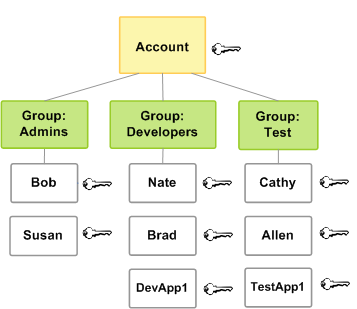 Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity Provider (idP) is
connected to AWS SSO as a part of federated access. E.g. the Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `amazonaws.com`. Services, as trusted enitites, assume
roles to gain permissions.
A `*` represents every principal. Set the `*` to make an instance of a service
public through the Internet.
The IAM is not necessarily used by S3. AK/SK is sufficient for authentication
and authorization.
* An AWS unqiue Account ID has a length of 12 digits.
* Access key ID, starts with `AKIA` + 20 chars
* Secret access key (SK)
* Session token, `ASIA` + sessionToken
* AWS Organizations control accounts who joined
* Third party identity providers are supported
* IAM identity center of an organization allows provision of accounts from third parties through the AWS SSO
### Root Accounts
Every AWS account has a single root account bound to an email address, which is
also the username. This account has got the all privileges over the account. A
root account has MFA disabled by default.
It has all permissions except Organizational Service Control Policies.
The account is susceptible to an attack if the mail address is accessible but
MFA is not activated.
The email address of the root account, which is called `MasterAccountEmail` can
be found as member of an AWS Organization
```sh
aws organizations describe-organization
```
If the MFA is not set, it is an opportunity for a password reset attack when
the account the vulnerable root belongs to is part of an AWS Organization.
If the email address is also linked to an Amazon retail account and it is
shared between people, everyone has full root access.
### (User) Policies
Policies are an authorization measurement. After authentication of a user (or
principal) policies of the account are checked if the request is allowed.
A policy may also be attached to a resource. Policy evaluation can be found in the [AWS docs](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_evaluation-logic.html).
```sh
aws iam get-policy
```
Policy details consists of the following [example](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements.html)
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
```
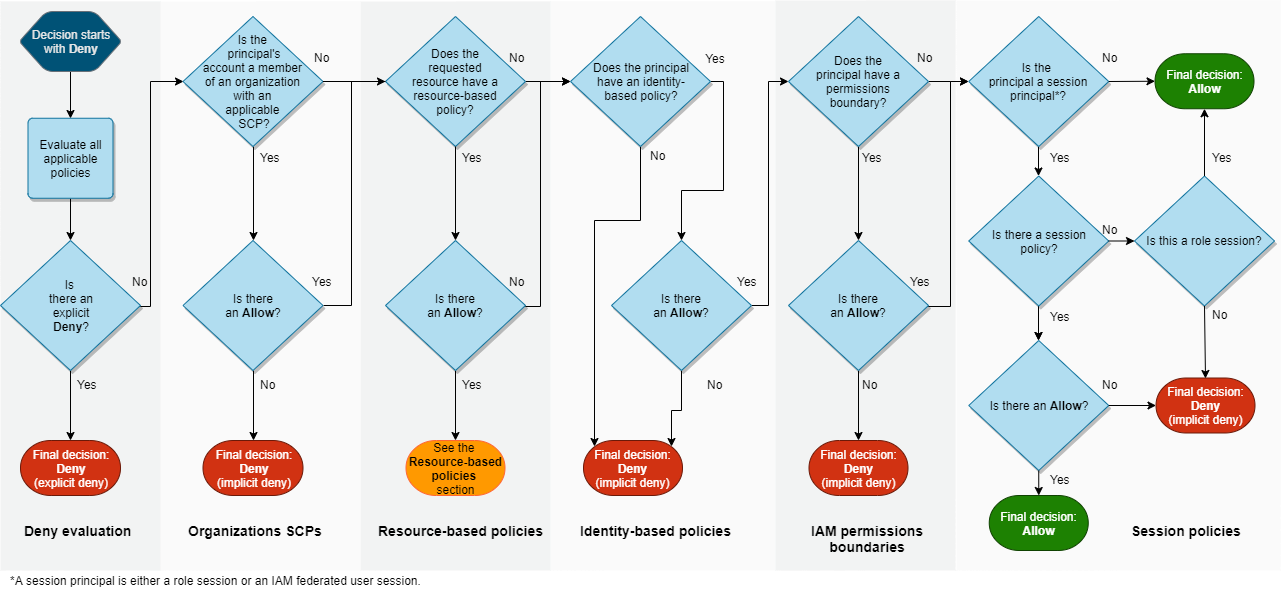
The following graph is taken from the documentation, it shows the evaluation
logic inside an account
Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity Provider (idP) is
connected to AWS SSO as a part of federated access. E.g. the Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `amazonaws.com`. Services, as trusted enitites, assume
roles to gain permissions.
A `*` represents every principal. Set the `*` to make an instance of a service
public through the Internet.
The IAM is not necessarily used by S3. AK/SK is sufficient for authentication
and authorization.
* An AWS unqiue Account ID has a length of 12 digits.
* Access key ID, starts with `AKIA` + 20 chars
* Secret access key (SK)
* Session token, `ASIA` + sessionToken
* AWS Organizations control accounts who joined
* Third party identity providers are supported
* IAM identity center of an organization allows provision of accounts from third parties through the AWS SSO
### Root Accounts
Every AWS account has a single root account bound to an email address, which is
also the username. This account has got the all privileges over the account. A
root account has MFA disabled by default.
It has all permissions except Organizational Service Control Policies.
The account is susceptible to an attack if the mail address is accessible but
MFA is not activated.
The email address of the root account, which is called `MasterAccountEmail` can
be found as member of an AWS Organization
```sh
aws organizations describe-organization
```
If the MFA is not set, it is an opportunity for a password reset attack when
the account the vulnerable root belongs to is part of an AWS Organization.
If the email address is also linked to an Amazon retail account and it is
shared between people, everyone has full root access.
### (User) Policies
Policies are an authorization measurement. After authentication of a user (or
principal) policies of the account are checked if the request is allowed.
A policy may also be attached to a resource. Policy evaluation can be found in the [AWS docs](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_evaluation-logic.html).
```sh
aws iam get-policy
```
Policy details consists of the following [example](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements.html)
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
```
The following graph is taken from the documentation, it shows the evaluation
logic inside an account
 A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a policy represents every principal. Set the `*` to make an instance of a service
public through the Internet.
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Sanity test a profile through checking its existance via
```sh
aws iam list-users
aws s3 ls --profile PROFILENAME
```
Find account ID to an access key
```sh
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
```
Find username to an access key
```sh
aws sts get-caller-identity --profile PROFILENAME
```
Listing EC2 instances of an account
```sh
aws ec2 describe-instances --output text --profile PROFILENAME
```
In another region
```sh
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
```
### Secrets
```sh
aws secretsmanager help
aws secretsmanager list-secrets
ws secretsmanager get-secret-value --secret-id --region
```
### Amazon Resource Name (ARN)
The [ARN](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference-arns.html)
is a unique ID which identifies resources.
A Unique ID is create through the following scheme
```sh
arn:aws::::/
```
## Services
An [action on an
API](https://docs.aws.amazon.com/service-authorization-/latest/reference/reference_policies_actions-resources-contextkeys.html)
of a service is structured like `:`.
### Virtual Private Cloud (VPC)
Is a logic network segementation method using its own IP address range.
Contains EC2 VMs and has an Internet gateway if needed. The
gateway can be either just ingress, egress, or both. EC2 can use elastic IP
addresses to provide Ingress. A Gateway Load Balancer can be used to do traffic inspection.
A VPC is part of the EC2 namespace `ec2:CreateVPC`
To connect to a VPC, it does not need to be exposed to the Internet. It is
accessible through various connection services like Direct Connect or
PrivateLink.
VPCs can have multiple subnets, they use host infrastructure components like
DHCP, NTP and DNS provided by AWS.
NTP can be found under 169.254.169.123. The DNS resolver `Route 53` can be
found under 169.254.169.253. Microsoft's KMS service can be at 169.254.169.250
and 169.254.169.251.
#### Metadata Service
The instance (Openstack) Metadata service can be found under 169.254.169.254.
It can be used
to gain information about the EC2 via a GET request to
http://169.254.169.254/latest/meta-data .
The task metadata service can be found at 169.254.170.2 and is used for the
Elastic Container Service (ECS).
The instance metadata service has been used for information disclosure of
security credentials before.
[Alexander
Hose](https://alexanderhose.com/how-to-hack-aws-instances-with-the-metadata-service-enabled/)
describes how to use the credentials through aws-cli.
```sh
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
ec2S3FullAccess
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/ec2S3FullAccess
{
"Code": "Success",
"LastUpdated": "2022-10-01T15:19:43Z",
"Type": "AWS-HMAC",
"AccessKeyId": "ASIAMFKOAUSJ7EXAMPLE",
"SecretAccessKey": "UeEevJGByhEXAMPLEKEY",
"Token": "TQijaZw==",
"Expiration": "2022-10-01T21:44:45Z"
}
```
Use the credentials to configure aws-cli.
```sh
$ aws configure
AWS Access Key ID [None]: ASIAMFKOAUSJ7EXAMPLE
AWS Secret Access Key [None]: UeEevJGByhEXAMPLEKEYEXAMPLEKEY
Default region name [None]: us-east-2
Default output format [None]: json
```
Add the credentials to the AWS credentials file
```sh
[default]
aws_access_key_id = ASIAMFKOAUSJ7EXAMPLE
aws_secret_access_key = UeEevJGByhEXAMPLEKEYEXAMPLEKEY
aws_session_token = TQijaZw==
```
### Simple Storage Service (S3)
[S3](https://aws.amazon.com/s3/) is an object storage without volume limits.
The names of buckets are unique and the namespace of buckets is global but they
are stored regionally.
Methods of access control are as follows
1. [Bucket policies](https://docs.aws.amazon.com/AmazonS3/latest/userguide/bucket-policies.html)
2. [S3 ACL](https://docs.aws.amazon.com/AmazonS3/latest/userguide/managing-acls.html)
The aws cli scheme is
```sh
http://.s3.amazonaws.com/file.name
```
or
```sh
http://s3.amazonaws.com/BUCKETNAME/FILENAME.ext
```
#### Check Permissions of a bucket
Do a `PUT` method to see if the bucket may be writeable to upload a file via
```sh
curl -vvv -X PUT $BUCKET_URL --data "Test of write permissions"
```
#### List content of public bucket via
```sh
aws s3 ls s3:/// --no-sign-request
```
Download via `curl`, `wget` or `s3` cli via
```sh
aws s3 cp s3:///foo_public.xml . --no-sign-request
```
#### ACL
If the ACL is set to
* `Anyone`, just `curl`
* `AuthenticatedUsers`, `s3` cli with aws key
A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a policy represents every principal. Set the `*` to make an instance of a service
public through the Internet.
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Sanity test a profile through checking its existance via
```sh
aws iam list-users
aws s3 ls --profile PROFILENAME
```
Find account ID to an access key
```sh
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
```
Find username to an access key
```sh
aws sts get-caller-identity --profile PROFILENAME
```
Listing EC2 instances of an account
```sh
aws ec2 describe-instances --output text --profile PROFILENAME
```
In another region
```sh
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
```
### Secrets
```sh
aws secretsmanager help
aws secretsmanager list-secrets
ws secretsmanager get-secret-value --secret-id --region
```
### Amazon Resource Name (ARN)
The [ARN](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference-arns.html)
is a unique ID which identifies resources.
A Unique ID is create through the following scheme
```sh
arn:aws::::/
```
## Services
An [action on an
API](https://docs.aws.amazon.com/service-authorization-/latest/reference/reference_policies_actions-resources-contextkeys.html)
of a service is structured like `:`.
### Virtual Private Cloud (VPC)
Is a logic network segementation method using its own IP address range.
Contains EC2 VMs and has an Internet gateway if needed. The
gateway can be either just ingress, egress, or both. EC2 can use elastic IP
addresses to provide Ingress. A Gateway Load Balancer can be used to do traffic inspection.
A VPC is part of the EC2 namespace `ec2:CreateVPC`
To connect to a VPC, it does not need to be exposed to the Internet. It is
accessible through various connection services like Direct Connect or
PrivateLink.
VPCs can have multiple subnets, they use host infrastructure components like
DHCP, NTP and DNS provided by AWS.
NTP can be found under 169.254.169.123. The DNS resolver `Route 53` can be
found under 169.254.169.253. Microsoft's KMS service can be at 169.254.169.250
and 169.254.169.251.
#### Metadata Service
The instance (Openstack) Metadata service can be found under 169.254.169.254.
It can be used
to gain information about the EC2 via a GET request to
http://169.254.169.254/latest/meta-data .
The task metadata service can be found at 169.254.170.2 and is used for the
Elastic Container Service (ECS).
The instance metadata service has been used for information disclosure of
security credentials before.
[Alexander
Hose](https://alexanderhose.com/how-to-hack-aws-instances-with-the-metadata-service-enabled/)
describes how to use the credentials through aws-cli.
```sh
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
ec2S3FullAccess
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/ec2S3FullAccess
{
"Code": "Success",
"LastUpdated": "2022-10-01T15:19:43Z",
"Type": "AWS-HMAC",
"AccessKeyId": "ASIAMFKOAUSJ7EXAMPLE",
"SecretAccessKey": "UeEevJGByhEXAMPLEKEY",
"Token": "TQijaZw==",
"Expiration": "2022-10-01T21:44:45Z"
}
```
Use the credentials to configure aws-cli.
```sh
$ aws configure
AWS Access Key ID [None]: ASIAMFKOAUSJ7EXAMPLE
AWS Secret Access Key [None]: UeEevJGByhEXAMPLEKEYEXAMPLEKEY
Default region name [None]: us-east-2
Default output format [None]: json
```
Add the credentials to the AWS credentials file
```sh
[default]
aws_access_key_id = ASIAMFKOAUSJ7EXAMPLE
aws_secret_access_key = UeEevJGByhEXAMPLEKEYEXAMPLEKEY
aws_session_token = TQijaZw==
```
### Simple Storage Service (S3)
[S3](https://aws.amazon.com/s3/) is an object storage without volume limits.
The names of buckets are unique and the namespace of buckets is global but they
are stored regionally.
Methods of access control are as follows
1. [Bucket policies](https://docs.aws.amazon.com/AmazonS3/latest/userguide/bucket-policies.html)
2. [S3 ACL](https://docs.aws.amazon.com/AmazonS3/latest/userguide/managing-acls.html)
The aws cli scheme is
```sh
http://.s3.amazonaws.com/file.name
```
or
```sh
http://s3.amazonaws.com/BUCKETNAME/FILENAME.ext
```
#### Check Permissions of a bucket
Do a `PUT` method to see if the bucket may be writeable to upload a file via
```sh
curl -vvv -X PUT $BUCKET_URL --data "Test of write permissions"
```
#### List content of public bucket via
```sh
aws s3 ls s3:/// --no-sign-request
```
Download via `curl`, `wget` or `s3` cli via
```sh
aws s3 cp s3:///foo_public.xml . --no-sign-request
```
#### ACL
If the ACL is set to
* `Anyone`, just `curl`
* `AuthenticatedUsers`, `s3` cli with aws key
 A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a policy represents every principal. Set the `*` to make an instance of a service
public through the Internet.
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Sanity test a profile through checking its existance via
```sh
aws iam list-users
aws s3 ls --profile PROFILENAME
```
Find account ID to an access key
```sh
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
```
Find username to an access key
```sh
aws sts get-caller-identity --profile PROFILENAME
```
Listing EC2 instances of an account
```sh
aws ec2 describe-instances --output text --profile PROFILENAME
```
In another region
```sh
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
```
### Secrets
```sh
aws secretsmanager help
aws secretsmanager list-secrets
ws secretsmanager get-secret-value --secret-id
A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a policy represents every principal. Set the `*` to make an instance of a service
public through the Internet.
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Sanity test a profile through checking its existance via
```sh
aws iam list-users
aws s3 ls --profile PROFILENAME
```
Find account ID to an access key
```sh
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
```
Find username to an access key
```sh
aws sts get-caller-identity --profile PROFILENAME
```
Listing EC2 instances of an account
```sh
aws ec2 describe-instances --output text --profile PROFILENAME
```
In another region
```sh
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
```
### Secrets
```sh
aws secretsmanager help
aws secretsmanager list-secrets
ws secretsmanager get-secret-value --secret-id  Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity Provider (idP) is
connected to AWS SSO as a part of federated access. E.g. the Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `
Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity Provider (idP) is
connected to AWS SSO as a part of federated access. E.g. the Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `