# AWS Enumeration
## Regions
[A list of services by
region](https://aws.amazon.com/about-aws/global-infrastructure/regional-product-services/)
is maintained by AWS
There are global and regional services.
Watch out for the global and regional __Security Token Service__ (STS) which
provides temporary access to third party identities, since regional STS are
also valid in other regions. Global STS are only valid in default regions.
In aws cli,
[Regions](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/using-regions-availability-zones.html#concepts-available-segions)
got
the cli argument `--region`
## Identity Access Management (IAM)
Permissions are granted directly through IAM identities (IAM Principals) inside
an AWS account or indirectly through
groups and roles the principal (user or service) has joined.
```sh
aws iam list-users
```
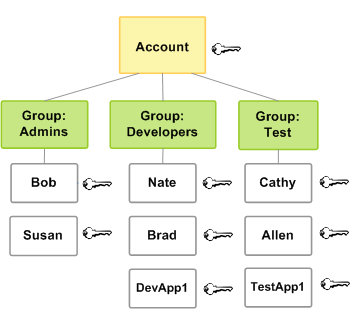 Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity
Provider (idP) is connected to AWS SSO as a part of federated access. E.g. the
Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `amazonaws.com`. Services, as trusted enitites, assume
roles to gain permissions.
A `*` represents every principal. Set the `*` to make an instance of a service
public through the Internet.
Identify an unknown accountname by using an access key
```sh
aws sts get-access-key-info --access-key
```
The IAM is not necessarily used by S3. AK/SK is sufficient for authentication
and authorization.
* AWS got [unique ID prefixes](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_identifiers.html#identifiers-prefixes)
* An AWS unqiue Account ID has a length of 12 digits.
* Longterm Access key ID, starts with `AKIA` + 20 chars
* Secret access key (SK)
* Shortterm Session token, `ASIA` + sessionToken
* AWS Organizations control accounts who joined
* Third party identity providers are supported
* IAM identity center of an organization allows provision of accounts from third parties through the AWS SSO
### Root Accounts
Every AWS account has a single root account bound to an email address, which is
also the username. This account has got the all privileges over the account. A
root account has MFA disabled by default.
It has all permissions except Organizational Service Control Policies.
The account is susceptible to an attack if the mail address is accessible but
MFA is not activated.
The email address of the root account, which is called `MasterAccountEmail` can
be found as member of an AWS Organization
```sh
aws organizations describe-organization
```
If the MFA is not set, it is an opportunity for a password reset attack when
the account the vulnerable root belongs to is part of an AWS Organization.
If the email address is also linked to an Amazon retail account and it is
shared between people, everyone has full root access.
### Principal, Resource & Service Policies
Policies are an authorization measurement. After authentication of a user (or
principal) policies of the account are checked if the request is allowed.
A policy may also be attached to a resource or (in an organization) a service.
Policy evaluation can be found in
the [AWS
docs](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_evaluation-logic.html).
There are resource and identity based policies.
```sh
aws iam get-policy --policy-arn
```
Policy details consists of the following [example](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements.html)
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
```
Policy enforcement is done via the `Effect` keys and either has `allow` or
`deny` keys set in the JSON object. Deny is default.
The `Action` keyword contains a Service and an API keyword on on that service
in the scheme `:`, e.g.
`"Action":["ec2:Get*","ec2:Describe*", "s3:*"]`. See the [Service Authorization
Docs](https://docs.aws.amazon.com/service-authorization/latest/reference/)
The Resource key contains the ARN of the resource the policy is set for.
The `Principal` key is only set for resource policies and contains the
principal who is able to act on the resource. For example a `*` value allows
public access.
[Operators](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_condition_operators.html)
can be used to set conditions [using key value pairs inside
policies](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_condition-keys.html)
```json
"Condition": {
"IPAddressIfExists": {"aws:SourceIp": ["xxx"] },
"StringEqualsIfExists": {"aws:sourceVpc": ["yyy"]}
}
```
Principals, resources and actions can also be excluded specifically through
`NotPrincipal`, `NotResource` and `NotAction`.
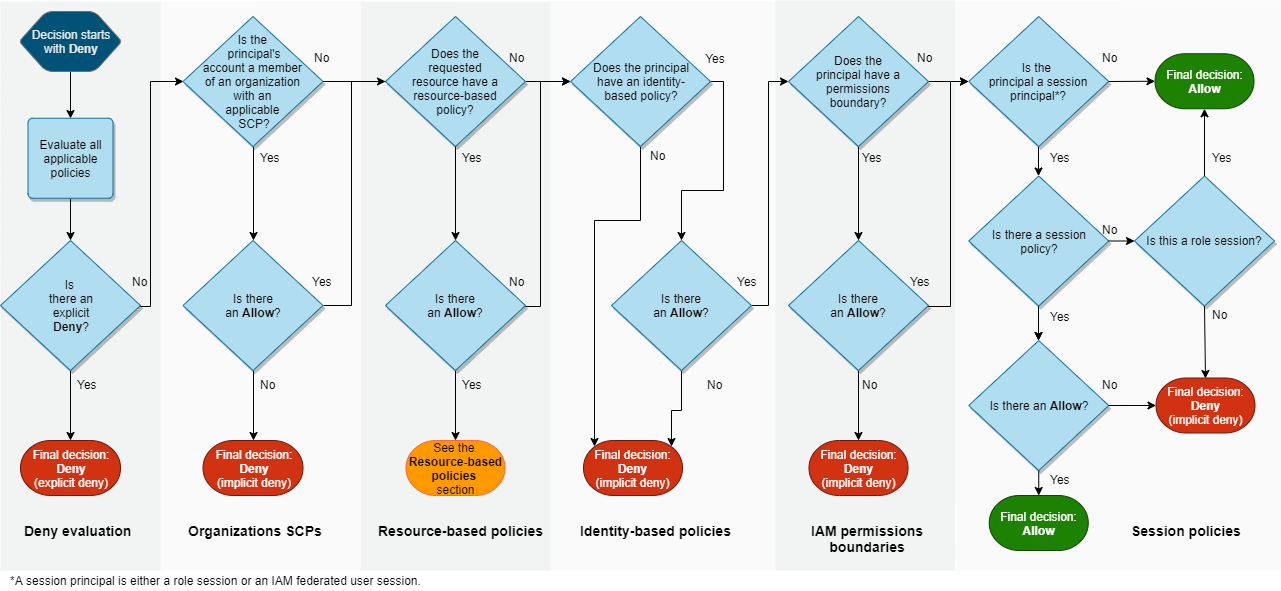
The following graph is taken from the documentation, it shows the evaluation
logic inside an account
Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity
Provider (idP) is connected to AWS SSO as a part of federated access. E.g. the
Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `amazonaws.com`. Services, as trusted enitites, assume
roles to gain permissions.
A `*` represents every principal. Set the `*` to make an instance of a service
public through the Internet.
Identify an unknown accountname by using an access key
```sh
aws sts get-access-key-info --access-key
```
The IAM is not necessarily used by S3. AK/SK is sufficient for authentication
and authorization.
* AWS got [unique ID prefixes](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_identifiers.html#identifiers-prefixes)
* An AWS unqiue Account ID has a length of 12 digits.
* Longterm Access key ID, starts with `AKIA` + 20 chars
* Secret access key (SK)
* Shortterm Session token, `ASIA` + sessionToken
* AWS Organizations control accounts who joined
* Third party identity providers are supported
* IAM identity center of an organization allows provision of accounts from third parties through the AWS SSO
### Root Accounts
Every AWS account has a single root account bound to an email address, which is
also the username. This account has got the all privileges over the account. A
root account has MFA disabled by default.
It has all permissions except Organizational Service Control Policies.
The account is susceptible to an attack if the mail address is accessible but
MFA is not activated.
The email address of the root account, which is called `MasterAccountEmail` can
be found as member of an AWS Organization
```sh
aws organizations describe-organization
```
If the MFA is not set, it is an opportunity for a password reset attack when
the account the vulnerable root belongs to is part of an AWS Organization.
If the email address is also linked to an Amazon retail account and it is
shared between people, everyone has full root access.
### Principal, Resource & Service Policies
Policies are an authorization measurement. After authentication of a user (or
principal) policies of the account are checked if the request is allowed.
A policy may also be attached to a resource or (in an organization) a service.
Policy evaluation can be found in
the [AWS
docs](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_evaluation-logic.html).
There are resource and identity based policies.
```sh
aws iam get-policy --policy-arn
```
Policy details consists of the following [example](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements.html)
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListAllMyBuckets",
"Resource": "*"
}
]
}
```
Policy enforcement is done via the `Effect` keys and either has `allow` or
`deny` keys set in the JSON object. Deny is default.
The `Action` keyword contains a Service and an API keyword on on that service
in the scheme `:`, e.g.
`"Action":["ec2:Get*","ec2:Describe*", "s3:*"]`. See the [Service Authorization
Docs](https://docs.aws.amazon.com/service-authorization/latest/reference/)
The Resource key contains the ARN of the resource the policy is set for.
The `Principal` key is only set for resource policies and contains the
principal who is able to act on the resource. For example a `*` value allows
public access.
[Operators](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_condition_operators.html)
can be used to set conditions [using key value pairs inside
policies](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_condition-keys.html)
```json
"Condition": {
"IPAddressIfExists": {"aws:SourceIp": ["xxx"] },
"StringEqualsIfExists": {"aws:sourceVpc": ["yyy"]}
}
```
Principals, resources and actions can also be excluded specifically through
`NotPrincipal`, `NotResource` and `NotAction`.
The following graph is taken from the documentation, it shows the evaluation
logic inside an account
 A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a "Principal" value represents every principal. Set the `*` to
make an instance of a service public through the Internet like this following rule.
```json
"Principal": {
"AWS": "*"
}
```
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
The `AdministratorAccess` policy looks like this
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Set a session token for the profile
```sh
aws configure --profile PROFILENAME set aws_session_token
```
Sanity test a profile through checking its existance via
```sh
aws iam list-users
aws s3 ls --profile PROFILENAME
```
Find account ID to an access key
```sh
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
```
List the (current) user details
```sh
aws sts get-caller-identity
aws sts --profile get-caller-identity
```
Find username to an access key
```sh
aws sts get-caller-identity --profile PROFILENAME
```
List EC2 instances of an account
```sh
aws ec2 describe-instances --output text --profile PROFILENAME
```
In another region
```sh
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
```
Create a user via cloudshell.
```sh
aws iam create-user --user-name
```
Add a user to a group via cloudshell.
```sh
aws iam add-user-to-group --user-name --group-name
```
List groups for a user using aws cli. GroupIds begin with `AGPA`.
```sh
aws iam list-groups-for-user --user-name padawan
```
### Credentials
User credentials are called profiles on the webUI and console
Password is used by the aws cli tool and queried APIs.
Create a user password via aws cli
```sh
aws iam create-login-profile --user --password
```
Change the password using the aws cli
```sh
aws iam update-login-profile --user --password
```
Take a look at the password policy via aws cli
```sh
aws iam get-account-password-policy
```
### API Access Keys
Longterm, non-expiring Access key ID start with `AKIA` + 20 chars
List the access keys via aws cli.
```sh
aws iam list-access-keys
```
Create an access key via the aws cli.
```sh
aws iam create-access-key --user-name
```
Disable, enable or delete an access key via the aws cli
```sh
aws iam update-access-key --access-key-id
aws iam update-access-key --access-key-id
aws iam delete-access-key --access-key-id
```
### Shortterm Session Keys (STS)
Session keys are short term, they expire. A session key start
with `ASIA`.
These are generated by the Security Token Service.
Use aws cli to create a session token through STS.
```sh
aws sts get-session-token
```
If you want to set a profile for a principal that has only an session token use this aws cli commands.
```sh
aws configure --profile PROFILENAME
aws configure --profile PROFILENAME set aws_session_token
```
Token can be applied to a user as a second factor. If the user is provided by another
federated entity through idP the MFA needs to be provided
through this solution.
List users with MFA enabled via aws cli.
```sh
aws iam list-virtual-mfa-devices
```
You can get the username of an account through the STS service using the access-key
```sh
aws sts get-access-key-info --access-key-id
```
The session token can be found via the cloudshell through the use of curl.
```sh
curl -H "X-aws-ec2-metadata-token: $AWS_CONTAINER_AUTHORIZATION_TOKEN" $AWS_CONTAINER_CREDENTIALS_FULL_URI
```
#### Assume Roles through STS
A an attack vector, a user can assume a role of higher privileges through the STS. This might happen through a policy bound to a group the user is a member of.
You need an ARN of the role you want to assume
```sh
arn:aws:iam:::role/
```
A role session name from the CloudTrail logs is needed, somone who has got the role we want to assume.
Use aws cli to assume the role.
```sh
aws --profile sts assume-role --role-arn arn:aws:iam:::role/ --role-session-name
```
This result of this is to get the `AccessKeyId`, `SecretAccessKey` and `SessionToken` of the user to complete the three needed variables for aquiring the high privilege.
```sh
export AWS_SECRET_ACCESS_KEY=
export AWS_ACCESS_KEY_ID=
export AWS_SESSION_TOKEN=
```
Check the current identity after setting the variables via aws cli.
```sh
aws sts get-caller-identity
```
### Secrets
Use the secrets manager via
```sh
aws secretsmanager help
aws secretsmanager list-secrets
aws secretsmanager get-secret-value --secret-id --region
```
### Amazon Resource Name (ARN)
The [ARN](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference-arns.html)
is a unique ID which identifies resources.
A Unique ID is create through the following scheme
```sh
arn:aws::::/
```
## Services
An [action on an
API](https://docs.aws.amazon.com/service-authorization-/latest/reference/reference_policies_actions-resources-contextkeys.html)
of a service is structured like `:`.
Session tokens can also be created for services for temporary access of
resources. This can be done through metadata service on an EC2 instance. The
session token and AK/SK are also visible in the environment variables of AWS
Lambda.
The session token can be found via the cloudshell through the use of curl.
```sh
curl -H "X-aws-ec2-metadata-token: $AWS_CONTAINER_AUTHORIZATION_TOKEN" $AWS_CONTAINER_CREDENTIALS_FULL_URI
```
### Virtual Private Cloud (VPC)
Is a logic network segementation method using its own IP address range.
Contains EC2 VMs and has an Internet gateway if needed. The
gateway can be either just ingress, egress, or both. EC2 can use elastic IP
addresses to provide Ingress. A Gateway Load Balancer can be used to do traffic inspection.
A VPC is part of the EC2 namespace `ec2:CreateVPC`
To connect to a VPC, it does not need to be exposed to the Internet. It is
accessible through various connection services like Direct Connect or
PrivateLink.
VPCs can have multiple subnets, they use host infrastructure components like
DHCP, NTP and DNS provided by AWS.
NTP can be found under 169.254.169.123. The DNS resolver `Route 53` can be
found under 169.254.169.253. Microsoft's KMS service can be at 169.254.169.250
and 169.254.169.251.
#### Metadata Service
The instance (Openstack) Metadata service can be found under 169.254.169.254.
It can be used
to gain information about the EC2 via a GET request to
`http://169.254.169.254/latest/meta-data`.
The task metadata service can be found at 169.254.170.2 and is used for the
[Elastic Container Service (ECS)](https://docs.aws.amazon.com/AmazonECS/latest/developerguide/task-iam-roles.html)
From inside a container curl can be used to get the credentials
```sh
curl 169.254.170.2$AWS_CONTAINER_CREDENTIALS_RELATIVE_URI
```
The instance metadata service has been used for information disclosure of
security credentials before.
[Alexander
Hose](https://alexanderhose.com/how-to-hack-aws-instances-with-the-metadata-service-enabled/)
describes how to use the credentials through aws-cli.
```sh
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
ec2S3FullAccess
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/ec2S3FullAccess
{
"Code": "Success",
"LastUpdated": "2022-10-01T15:19:43Z",
"Type": "AWS-HMAC",
"AccessKeyId": "ASIAMFKOAUSJ7EXAMPLE",
"SecretAccessKey": "UeEevJGByhEXAMPLEKEY",
"Token": "TQijaZw==",
"Expiration": "2022-10-01T21:44:45Z"
}
```
Use the credentials to configure aws-cli.
```sh
$ aws configure
AWS Access Key ID [None]: ASIAMFKOAUSJ7EXAMPLE
AWS Secret Access Key [None]: UeEevJGByhEXAMPLEKEYEXAMPLEKEY
Default region name [None]: us-east-2
Default output format [None]: json
```
Add the credentials to the AWS credentials file
```sh
[default]
aws_access_key_id = ASIAMFKOAUSJ7EXAMPLE
aws_secret_access_key = UeEevJGByhEXAMPLEKEYEXAMPLEKEY
aws_session_token = TQijaZw==
```
### Simple Storage Service (S3)
[S3](https://aws.amazon.com/s3/) is an object storage without volume limits.
A nested directory structure in a bucket is possible,
but pseudo file system for organizing files.
The names of buckets are unique and the namespace of
buckets is global but they are stored regionally.
Versioning of files is possible. Files will not be
overwritten by updated versions. Files are enrypted by
default.
Methods of access control are as follows
1. [Bucket policies](https://docs.aws.amazon.com/AmazonS3/latest/userguide/bucket-policies.html)
2. [S3 ACL](https://docs.aws.amazon.com/AmazonS3/latest/userguide/managing-acls.html)
Every bucket that was created before November 2018 has a default public access
permissions. Since November 2018 public access is blocked by default.
A typical attack includes modifying files on a bucket another service is using.
#### S3 Policies
Useful permissions to an attack, set through a policy, are `s3:GetObject` and `s3:PutObject`.
There are identity based and resource based policies for s3 buckets.
If global access or read is set, a resource based
policy access to the objects is available in general of everyone, unauthenticated.
```json
{
[...]
"Effect": "Allow",
"Principal": "*",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
[...]
}
```
Check which policies are set
```sh
aws s3api get-bucket-policy-status --bucket
aws s3api get-bucket-ownership-controls --bucket
```
#### ACL
Existed since before AWS IAM. The ACL is generated for
every bucket created. Resource owner gets full
permissions. ACL can be extended through principals'
[canonical
userID](https://docs.aws.amazon.com/AmazonS3/latest/userguide/finding-canonical-user-id.html)
and services which are allowed or forbidden to access
the bucket.
__Attack vector__: The group `Any Authenticated AWS
User` can be set as permissions for a group of every
authenticated AWS user.
If the ACL is set to
* `Anyone`, just `curl`
* `AuthenticatedUsers`, `s3` cli with aws key
#### Scheme
The aws cli scheme for s3 is the following.
```sh
http://.s3.amazonaws.com/file.name
```
or
```sh
http://s3.amazonaws.com/BUCKETNAME/FILENAME.ext
```
#### Check Read Permissions of a bucket
Use the aws cli to store data from a bucket locally.
```sh
aws s3 sync --no-sign-request s3:// .
#### Check Permissions of a bucket
Use a `PUT` method to see if the bucket may be writeable to upload a file via
```sh
curl -vvv -X PUT $BUCKET_URL --data "Test of write permissions"
```
#### List content of public bucket via
```sh
aws s3 ls s3:/// --no-sign-request
```
Download via `curl`, `wget` or `s3` cli via
```sh
aws s3 cp s3:///foo_public.xml . --no-sign-request
```
### Lambda
Execute a lambda function via aws cli.
```sh
aws lambda invoke \
--function-name arn:aws:lambda:::function:
```
List policies
```sh
aws lambda get-policy \
--function-name arn:aws:lambda:::function: \
--query Policy \
--output text \
| jq .
```
### CloudFront
CloudFront is a Content Delivery Network(CDN), which stores static data on Edge
Locations, closer to the customer for performance improvements.
Geo-fences can be placed to access the content. Can also use authorization
based requests,encryption of data is possible.
A Web Application Firewall (WAF) as well as Distributed Denial of Service
(DDoS) prevention can be configured for CloudFront instances.
#### CloudFront Hosts
An "origin" of a CloudFront instance can be resources like EC2, ELBs or S3 buckets.
Origin Access Identities (OAIs), which are resourced based policies for the
resources or "origins" of a CloudFront instance, need to be set the owner.
For an attack to take place, information about the DNS records of a domain is
needed, to find probable CloudFront resources.
Use dig or drill or nslookup to list IP addresses of a (sub-)domain where
assets are hosted, potentially. Do A reverse lookup to get the aws domains of
the resources behind the IP addresses.
```sh
drill assets.example.com
drill <$IP_ADDRESS> -x
```
How to find a potentially interesting CloudFront assets domain
* Enumerate subdomains of a website
* Do some dorking with a search engine to list the content of a bucket behind an S3 subdomian
* Spider a website via wget or [Linkfinder](https://github.com/GerbenJavado/LinkFinder)
* Search for certificate details
### EC2
Deploy service instances of Virtual machines inside a VPC.
Deployment EC2 instances into 26 regions. Supports multiple OSs.
On-demand billing.
#### Connect to an EC2 Instance
Connect to the instance using SSH, RDP, SSM, serial console or webconsole.
A keypair is needed to be owned to connect, for eaxmple EC2 Connect uses
temporary keys. Serial Console has be activated by the adminstrator and
the user which will be used to login needs a password set.
The URL scheme for EC2 Connect through the webconsole is the following.
```sh
https://console.aws.amazon.com/ec2/v2/connect/$USERNAME/$INSTANCE_ID
```
| Method | Network Access needed | Requires Agent | Requires IAM Permissions |
+--------+-----------------------+----------------+--------------------------+
| SSH/RDP | YES | NO | NO |
| Instance Connect | YES | YES (amazon linux 2) | NO |
| SSM Run Command | No | YES | YES |
| SSM Session Manager | NO | YES | YES |
| Serial Console | No | Password needed | NO |
Instance Connect and the SSM Session Manager can be used to reset the root
password via `sudo passwd root`. After that it is possible to connect to the
root user, e.g. using serial console or just use `sudo su root` or `su root` directly.
#### EC2 and IAM
EC2 instances can use nearly any other service provided by AWS.
There only needs to be access to the credentials. This is can be done through
the Instance MetaData Service (IMDS). The IMDS is available through HTTP on
IP address `169.254.169.254` inside every EC2 instance.
##### Request Credentials through IMDS
There are two versions of IMDS in place right now.
Regardless of the version a name of a role needs to be requested through the
IMDS using curl, which is then used to query the token for said role.
###### Query IMDSv1 Permissions
Query the name of the role via curl.
```sh
role_name=$(curl -s http://169.254.169.254/latest/meta-data/iam/security-credentials/)
```
Through the knowledge of the role name we can request the credentials of that role.
```sh
curl -s http://169.254.169.254/latest/meta-data/iam/security-credentials/${role_name}
```
##### Query IMDSv2 Permissions
A token is needed to curl for the name of the role. This is done using curl.
```sh
TOKEN=$(curl -s -XPUT http://169.254.169.254/latest/api/token -H "X-aws-ec2-metadata-token-ttl-seconds: 21600")
```
The token is used to query the name of the role via curl.
```sh
role_name=$(curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/iam/security-credentials/)
```
Both, token and name of the role can then be used to request the credentials
via curl.
```sh
curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/iam/security-credentials/${role_name}
```
PS:
If you want to activate IMDSv2 an instance ID is needed to activate it through aws cli.
```sh
instance_id=$(curl -s http://169.254.169.254/latest/meta-data/instance-id)
region_name=
aws ec2 modify-instance-metadata-options --instance-id $instance_id --https-tokens required --region $region_name
```
#### EC2 & Elastic Network Interface (ENI)
Every EC2 instance has at least one ENI to be made available on the network.
There is a security group bound to each ENI to limit communication to the EC2
instance. Such security contain for example which IP addresses can access the
instance, on which ports and which protocols can be used to access it.
List available ENIs through the webshell of the account.
```sh
aws ec2 describe-network-interfaces
```
#### EC2 & ELastic Block Storage (EBS)
An EC2 instance has EBS as its set block device, either SSD or HDD.
EBS storage is persistent, snapshots can be created.
In contrast to other storage solutions. These other, ephemeral storage
solutions can not be snapshotted.
Snapshots can be created from EBSs, which are stored in S3 buckets.
Snapshots can be encrypted through KMS and can be shared accross accounts.
Snapshots deliver a lot of useful content.
List metadata of a snapshot via aws cli.
```sh
aws ec2 describe-snapshots --region --snapshot-ids
```
This shows the size of the volume in GBs, state of the drive, encryption, ownerId and so on.
A snapshot can be used to create a volume. Snapshots are available in a complete region after they got created, but they need to be in an explicit AZ to mount them.
Create a volume from a snapshot through metadata service on an EC2 instance using the following commands.
Get the current AZ through a metadata token.
```sh
TOKEN=$(curl -s -XPUT -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" http://169.254.169.254/latest/api/token
availability_zone=$(curl -s -H "X-aws-ec2-metdata-token: $TOKEN" http://169.254.169.254/latest/meta-data/placement/availability-zone)
```
A volume can be created with the use of the snapshot-id, the type, the region and the previously gathered AZ.
```sh
aws ec2 create-volume --snapshot-id --volume-type gp3 --region
--availability-zone $availability_zone
```
The output contains the `VolumeId` to attach the volume to an EC2 instance.
```sh
instance_id=$(curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id)
aws ec2 attach-volume --region --device /dev/sdh --instance-id $instance_id --volume-id
```
Mount the created and attached device to the file system
```sh
lsblk
sudo mkdir /mnt/attached-volume
sudo mount /dev/ /mnt/attached-volume
```
#### EC2 Amazon Machine Image (AMI) Configuration
An AMI is an image of a VM. This image can be configured before it is deployed via cloud-init scripts. These scripts may contain interesting data like credentials or other intel.
The files are stored in `/var/lib/cloud/instance/scripts/`
List all available or user specific AMIs on the account via aws cli.
```sh
aws ec2 describe-images
aws ec2 decribe-images --owners
```
Get the configuration file contents through Instance Connect to the EC2 or through the SSM Session Manager via curl.
```sh
TOKEN=$(curl -s -XPUT -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" http://169.254.169.254/latest/api/token
curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/user-data
```
Alternatively use aws cli to get the configuration files
```sh
TOKEN=$(curl -s -XPUT -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" http://169.254.169.254/latest/api/token
instance_id=$(curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id)
aws ec2 describe-instance-attribute --attribute UserData --instance-id $instance_id --region --query UserData --output text | base64 -d
```
#### Restore an Amazon Machine Image (AMI)
An EC2 VM can be created from an Amazon Machine Image,
that can be found in some S3 buckets.
```sh
aws ec2 create-restore-image-task --object-key --bucket --name
```
An `ImageId` will be returned. This `imageId` is needed to create the image later.
Create a keypair to connect to the created VM via SSH. the keypair is set for
EC2 instances by aws cli automatically.
```sh
aws ec2 create-key-pair --key-name --query "KeyMaterial" --output text > ./mykeys.pem
```
A subnet for the the creation of the ec2 is needed, pick one via aws cli.
```sh
aws ec2 describe-subnets
```
Further, a security group with SSH access is needed
```sh
aws ec2 describe-security-groups
```
Create an image including the found information
```sh
aws ec2 run-instances --image-id --instance-type t3a.micro --key-name --subnet-id --security-group-id
```
Take a look at the EC2 dashboard inside the webconsole to see the IP address of the created EC2 instance. Connect to the VM via SSH, using the generated keypair.
#### Elastic Loadbalancer (ELB)
* The AutoScaling Group (ASG) scales down the oldest instance.
* Only the Loadbalancer gets exposed, not the EC2 VMs.
* A ELB can terminate the TLS session.
* An Application ELB can have a WAF attached
List available load-balancers via aws cli.
```sh
aws elbv2 describe-load-balancers --query Loadbalancers[].DNSName --output text
```
A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a "Principal" value represents every principal. Set the `*` to
make an instance of a service public through the Internet like this following rule.
```json
"Principal": {
"AWS": "*"
}
```
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
The `AdministratorAccess` policy looks like this
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Set a session token for the profile
```sh
aws configure --profile PROFILENAME set aws_session_token
```
Sanity test a profile through checking its existance via
```sh
aws iam list-users
aws s3 ls --profile PROFILENAME
```
Find account ID to an access key
```sh
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
```
List the (current) user details
```sh
aws sts get-caller-identity
aws sts --profile get-caller-identity
```
Find username to an access key
```sh
aws sts get-caller-identity --profile PROFILENAME
```
List EC2 instances of an account
```sh
aws ec2 describe-instances --output text --profile PROFILENAME
```
In another region
```sh
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
```
Create a user via cloudshell.
```sh
aws iam create-user --user-name
```
Add a user to a group via cloudshell.
```sh
aws iam add-user-to-group --user-name --group-name
```
List groups for a user using aws cli. GroupIds begin with `AGPA`.
```sh
aws iam list-groups-for-user --user-name padawan
```
### Credentials
User credentials are called profiles on the webUI and console
Password is used by the aws cli tool and queried APIs.
Create a user password via aws cli
```sh
aws iam create-login-profile --user --password
```
Change the password using the aws cli
```sh
aws iam update-login-profile --user --password
```
Take a look at the password policy via aws cli
```sh
aws iam get-account-password-policy
```
### API Access Keys
Longterm, non-expiring Access key ID start with `AKIA` + 20 chars
List the access keys via aws cli.
```sh
aws iam list-access-keys
```
Create an access key via the aws cli.
```sh
aws iam create-access-key --user-name
```
Disable, enable or delete an access key via the aws cli
```sh
aws iam update-access-key --access-key-id
aws iam update-access-key --access-key-id
aws iam delete-access-key --access-key-id
```
### Shortterm Session Keys (STS)
Session keys are short term, they expire. A session key start
with `ASIA`.
These are generated by the Security Token Service.
Use aws cli to create a session token through STS.
```sh
aws sts get-session-token
```
If you want to set a profile for a principal that has only an session token use this aws cli commands.
```sh
aws configure --profile PROFILENAME
aws configure --profile PROFILENAME set aws_session_token
```
Token can be applied to a user as a second factor. If the user is provided by another
federated entity through idP the MFA needs to be provided
through this solution.
List users with MFA enabled via aws cli.
```sh
aws iam list-virtual-mfa-devices
```
You can get the username of an account through the STS service using the access-key
```sh
aws sts get-access-key-info --access-key-id
```
The session token can be found via the cloudshell through the use of curl.
```sh
curl -H "X-aws-ec2-metadata-token: $AWS_CONTAINER_AUTHORIZATION_TOKEN" $AWS_CONTAINER_CREDENTIALS_FULL_URI
```
#### Assume Roles through STS
A an attack vector, a user can assume a role of higher privileges through the STS. This might happen through a policy bound to a group the user is a member of.
You need an ARN of the role you want to assume
```sh
arn:aws:iam:::role/
```
A role session name from the CloudTrail logs is needed, somone who has got the role we want to assume.
Use aws cli to assume the role.
```sh
aws --profile sts assume-role --role-arn arn:aws:iam:::role/ --role-session-name
```
This result of this is to get the `AccessKeyId`, `SecretAccessKey` and `SessionToken` of the user to complete the three needed variables for aquiring the high privilege.
```sh
export AWS_SECRET_ACCESS_KEY=
export AWS_ACCESS_KEY_ID=
export AWS_SESSION_TOKEN=
```
Check the current identity after setting the variables via aws cli.
```sh
aws sts get-caller-identity
```
### Secrets
Use the secrets manager via
```sh
aws secretsmanager help
aws secretsmanager list-secrets
aws secretsmanager get-secret-value --secret-id --region
```
### Amazon Resource Name (ARN)
The [ARN](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference-arns.html)
is a unique ID which identifies resources.
A Unique ID is create through the following scheme
```sh
arn:aws::::/
```
## Services
An [action on an
API](https://docs.aws.amazon.com/service-authorization-/latest/reference/reference_policies_actions-resources-contextkeys.html)
of a service is structured like `:`.
Session tokens can also be created for services for temporary access of
resources. This can be done through metadata service on an EC2 instance. The
session token and AK/SK are also visible in the environment variables of AWS
Lambda.
The session token can be found via the cloudshell through the use of curl.
```sh
curl -H "X-aws-ec2-metadata-token: $AWS_CONTAINER_AUTHORIZATION_TOKEN" $AWS_CONTAINER_CREDENTIALS_FULL_URI
```
### Virtual Private Cloud (VPC)
Is a logic network segementation method using its own IP address range.
Contains EC2 VMs and has an Internet gateway if needed. The
gateway can be either just ingress, egress, or both. EC2 can use elastic IP
addresses to provide Ingress. A Gateway Load Balancer can be used to do traffic inspection.
A VPC is part of the EC2 namespace `ec2:CreateVPC`
To connect to a VPC, it does not need to be exposed to the Internet. It is
accessible through various connection services like Direct Connect or
PrivateLink.
VPCs can have multiple subnets, they use host infrastructure components like
DHCP, NTP and DNS provided by AWS.
NTP can be found under 169.254.169.123. The DNS resolver `Route 53` can be
found under 169.254.169.253. Microsoft's KMS service can be at 169.254.169.250
and 169.254.169.251.
#### Metadata Service
The instance (Openstack) Metadata service can be found under 169.254.169.254.
It can be used
to gain information about the EC2 via a GET request to
`http://169.254.169.254/latest/meta-data`.
The task metadata service can be found at 169.254.170.2 and is used for the
[Elastic Container Service (ECS)](https://docs.aws.amazon.com/AmazonECS/latest/developerguide/task-iam-roles.html)
From inside a container curl can be used to get the credentials
```sh
curl 169.254.170.2$AWS_CONTAINER_CREDENTIALS_RELATIVE_URI
```
The instance metadata service has been used for information disclosure of
security credentials before.
[Alexander
Hose](https://alexanderhose.com/how-to-hack-aws-instances-with-the-metadata-service-enabled/)
describes how to use the credentials through aws-cli.
```sh
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/
ec2S3FullAccess
[ec2-user ~] curl http://169.254.169.254/latest/meta-data/iam/security-credentials/ec2S3FullAccess
{
"Code": "Success",
"LastUpdated": "2022-10-01T15:19:43Z",
"Type": "AWS-HMAC",
"AccessKeyId": "ASIAMFKOAUSJ7EXAMPLE",
"SecretAccessKey": "UeEevJGByhEXAMPLEKEY",
"Token": "TQijaZw==",
"Expiration": "2022-10-01T21:44:45Z"
}
```
Use the credentials to configure aws-cli.
```sh
$ aws configure
AWS Access Key ID [None]: ASIAMFKOAUSJ7EXAMPLE
AWS Secret Access Key [None]: UeEevJGByhEXAMPLEKEYEXAMPLEKEY
Default region name [None]: us-east-2
Default output format [None]: json
```
Add the credentials to the AWS credentials file
```sh
[default]
aws_access_key_id = ASIAMFKOAUSJ7EXAMPLE
aws_secret_access_key = UeEevJGByhEXAMPLEKEYEXAMPLEKEY
aws_session_token = TQijaZw==
```
### Simple Storage Service (S3)
[S3](https://aws.amazon.com/s3/) is an object storage without volume limits.
A nested directory structure in a bucket is possible,
but pseudo file system for organizing files.
The names of buckets are unique and the namespace of
buckets is global but they are stored regionally.
Versioning of files is possible. Files will not be
overwritten by updated versions. Files are enrypted by
default.
Methods of access control are as follows
1. [Bucket policies](https://docs.aws.amazon.com/AmazonS3/latest/userguide/bucket-policies.html)
2. [S3 ACL](https://docs.aws.amazon.com/AmazonS3/latest/userguide/managing-acls.html)
Every bucket that was created before November 2018 has a default public access
permissions. Since November 2018 public access is blocked by default.
A typical attack includes modifying files on a bucket another service is using.
#### S3 Policies
Useful permissions to an attack, set through a policy, are `s3:GetObject` and `s3:PutObject`.
There are identity based and resource based policies for s3 buckets.
If global access or read is set, a resource based
policy access to the objects is available in general of everyone, unauthenticated.
```json
{
[...]
"Effect": "Allow",
"Principal": "*",
"Action": [
"s3:GetObject",
"s3:PutObject"
],
[...]
}
```
Check which policies are set
```sh
aws s3api get-bucket-policy-status --bucket
aws s3api get-bucket-ownership-controls --bucket
```
#### ACL
Existed since before AWS IAM. The ACL is generated for
every bucket created. Resource owner gets full
permissions. ACL can be extended through principals'
[canonical
userID](https://docs.aws.amazon.com/AmazonS3/latest/userguide/finding-canonical-user-id.html)
and services which are allowed or forbidden to access
the bucket.
__Attack vector__: The group `Any Authenticated AWS
User` can be set as permissions for a group of every
authenticated AWS user.
If the ACL is set to
* `Anyone`, just `curl`
* `AuthenticatedUsers`, `s3` cli with aws key
#### Scheme
The aws cli scheme for s3 is the following.
```sh
http://.s3.amazonaws.com/file.name
```
or
```sh
http://s3.amazonaws.com/BUCKETNAME/FILENAME.ext
```
#### Check Read Permissions of a bucket
Use the aws cli to store data from a bucket locally.
```sh
aws s3 sync --no-sign-request s3:// .
#### Check Permissions of a bucket
Use a `PUT` method to see if the bucket may be writeable to upload a file via
```sh
curl -vvv -X PUT $BUCKET_URL --data "Test of write permissions"
```
#### List content of public bucket via
```sh
aws s3 ls s3:/// --no-sign-request
```
Download via `curl`, `wget` or `s3` cli via
```sh
aws s3 cp s3:///foo_public.xml . --no-sign-request
```
### Lambda
Execute a lambda function via aws cli.
```sh
aws lambda invoke \
--function-name arn:aws:lambda:::function:
```
List policies
```sh
aws lambda get-policy \
--function-name arn:aws:lambda:::function: \
--query Policy \
--output text \
| jq .
```
### CloudFront
CloudFront is a Content Delivery Network(CDN), which stores static data on Edge
Locations, closer to the customer for performance improvements.
Geo-fences can be placed to access the content. Can also use authorization
based requests,encryption of data is possible.
A Web Application Firewall (WAF) as well as Distributed Denial of Service
(DDoS) prevention can be configured for CloudFront instances.
#### CloudFront Hosts
An "origin" of a CloudFront instance can be resources like EC2, ELBs or S3 buckets.
Origin Access Identities (OAIs), which are resourced based policies for the
resources or "origins" of a CloudFront instance, need to be set the owner.
For an attack to take place, information about the DNS records of a domain is
needed, to find probable CloudFront resources.
Use dig or drill or nslookup to list IP addresses of a (sub-)domain where
assets are hosted, potentially. Do A reverse lookup to get the aws domains of
the resources behind the IP addresses.
```sh
drill assets.example.com
drill <$IP_ADDRESS> -x
```
How to find a potentially interesting CloudFront assets domain
* Enumerate subdomains of a website
* Do some dorking with a search engine to list the content of a bucket behind an S3 subdomian
* Spider a website via wget or [Linkfinder](https://github.com/GerbenJavado/LinkFinder)
* Search for certificate details
### EC2
Deploy service instances of Virtual machines inside a VPC.
Deployment EC2 instances into 26 regions. Supports multiple OSs.
On-demand billing.
#### Connect to an EC2 Instance
Connect to the instance using SSH, RDP, SSM, serial console or webconsole.
A keypair is needed to be owned to connect, for eaxmple EC2 Connect uses
temporary keys. Serial Console has be activated by the adminstrator and
the user which will be used to login needs a password set.
The URL scheme for EC2 Connect through the webconsole is the following.
```sh
https://console.aws.amazon.com/ec2/v2/connect/$USERNAME/$INSTANCE_ID
```
| Method | Network Access needed | Requires Agent | Requires IAM Permissions |
+--------+-----------------------+----------------+--------------------------+
| SSH/RDP | YES | NO | NO |
| Instance Connect | YES | YES (amazon linux 2) | NO |
| SSM Run Command | No | YES | YES |
| SSM Session Manager | NO | YES | YES |
| Serial Console | No | Password needed | NO |
Instance Connect and the SSM Session Manager can be used to reset the root
password via `sudo passwd root`. After that it is possible to connect to the
root user, e.g. using serial console or just use `sudo su root` or `su root` directly.
#### EC2 and IAM
EC2 instances can use nearly any other service provided by AWS.
There only needs to be access to the credentials. This is can be done through
the Instance MetaData Service (IMDS). The IMDS is available through HTTP on
IP address `169.254.169.254` inside every EC2 instance.
##### Request Credentials through IMDS
There are two versions of IMDS in place right now.
Regardless of the version a name of a role needs to be requested through the
IMDS using curl, which is then used to query the token for said role.
###### Query IMDSv1 Permissions
Query the name of the role via curl.
```sh
role_name=$(curl -s http://169.254.169.254/latest/meta-data/iam/security-credentials/)
```
Through the knowledge of the role name we can request the credentials of that role.
```sh
curl -s http://169.254.169.254/latest/meta-data/iam/security-credentials/${role_name}
```
##### Query IMDSv2 Permissions
A token is needed to curl for the name of the role. This is done using curl.
```sh
TOKEN=$(curl -s -XPUT http://169.254.169.254/latest/api/token -H "X-aws-ec2-metadata-token-ttl-seconds: 21600")
```
The token is used to query the name of the role via curl.
```sh
role_name=$(curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/iam/security-credentials/)
```
Both, token and name of the role can then be used to request the credentials
via curl.
```sh
curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/iam/security-credentials/${role_name}
```
PS:
If you want to activate IMDSv2 an instance ID is needed to activate it through aws cli.
```sh
instance_id=$(curl -s http://169.254.169.254/latest/meta-data/instance-id)
region_name=
aws ec2 modify-instance-metadata-options --instance-id $instance_id --https-tokens required --region $region_name
```
#### EC2 & Elastic Network Interface (ENI)
Every EC2 instance has at least one ENI to be made available on the network.
There is a security group bound to each ENI to limit communication to the EC2
instance. Such security contain for example which IP addresses can access the
instance, on which ports and which protocols can be used to access it.
List available ENIs through the webshell of the account.
```sh
aws ec2 describe-network-interfaces
```
#### EC2 & ELastic Block Storage (EBS)
An EC2 instance has EBS as its set block device, either SSD or HDD.
EBS storage is persistent, snapshots can be created.
In contrast to other storage solutions. These other, ephemeral storage
solutions can not be snapshotted.
Snapshots can be created from EBSs, which are stored in S3 buckets.
Snapshots can be encrypted through KMS and can be shared accross accounts.
Snapshots deliver a lot of useful content.
List metadata of a snapshot via aws cli.
```sh
aws ec2 describe-snapshots --region --snapshot-ids
```
This shows the size of the volume in GBs, state of the drive, encryption, ownerId and so on.
A snapshot can be used to create a volume. Snapshots are available in a complete region after they got created, but they need to be in an explicit AZ to mount them.
Create a volume from a snapshot through metadata service on an EC2 instance using the following commands.
Get the current AZ through a metadata token.
```sh
TOKEN=$(curl -s -XPUT -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" http://169.254.169.254/latest/api/token
availability_zone=$(curl -s -H "X-aws-ec2-metdata-token: $TOKEN" http://169.254.169.254/latest/meta-data/placement/availability-zone)
```
A volume can be created with the use of the snapshot-id, the type, the region and the previously gathered AZ.
```sh
aws ec2 create-volume --snapshot-id --volume-type gp3 --region
--availability-zone $availability_zone
```
The output contains the `VolumeId` to attach the volume to an EC2 instance.
```sh
instance_id=$(curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id)
aws ec2 attach-volume --region --device /dev/sdh --instance-id $instance_id --volume-id
```
Mount the created and attached device to the file system
```sh
lsblk
sudo mkdir /mnt/attached-volume
sudo mount /dev/ /mnt/attached-volume
```
#### EC2 Amazon Machine Image (AMI) Configuration
An AMI is an image of a VM. This image can be configured before it is deployed via cloud-init scripts. These scripts may contain interesting data like credentials or other intel.
The files are stored in `/var/lib/cloud/instance/scripts/`
List all available or user specific AMIs on the account via aws cli.
```sh
aws ec2 describe-images
aws ec2 decribe-images --owners
```
Get the configuration file contents through Instance Connect to the EC2 or through the SSM Session Manager via curl.
```sh
TOKEN=$(curl -s -XPUT -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" http://169.254.169.254/latest/api/token
curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/user-data
```
Alternatively use aws cli to get the configuration files
```sh
TOKEN=$(curl -s -XPUT -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" http://169.254.169.254/latest/api/token
instance_id=$(curl -s -H "X-aws-ec2-metadata-token: $TOKEN" http://169.254.169.254/latest/meta-data/instance-id)
aws ec2 describe-instance-attribute --attribute UserData --instance-id $instance_id --region --query UserData --output text | base64 -d
```
#### Restore an Amazon Machine Image (AMI)
An EC2 VM can be created from an Amazon Machine Image,
that can be found in some S3 buckets.
```sh
aws ec2 create-restore-image-task --object-key --bucket --name
```
An `ImageId` will be returned. This `imageId` is needed to create the image later.
Create a keypair to connect to the created VM via SSH. the keypair is set for
EC2 instances by aws cli automatically.
```sh
aws ec2 create-key-pair --key-name --query "KeyMaterial" --output text > ./mykeys.pem
```
A subnet for the the creation of the ec2 is needed, pick one via aws cli.
```sh
aws ec2 describe-subnets
```
Further, a security group with SSH access is needed
```sh
aws ec2 describe-security-groups
```
Create an image including the found information
```sh
aws ec2 run-instances --image-id --instance-type t3a.micro --key-name --subnet-id --security-group-id
```
Take a look at the EC2 dashboard inside the webconsole to see the IP address of the created EC2 instance. Connect to the VM via SSH, using the generated keypair.
#### Elastic Loadbalancer (ELB)
* The AutoScaling Group (ASG) scales down the oldest instance.
* Only the Loadbalancer gets exposed, not the EC2 VMs.
* A ELB can terminate the TLS session.
* An Application ELB can have a WAF attached
List available load-balancers via aws cli.
```sh
aws elbv2 describe-load-balancers --query Loadbalancers[].DNSName --output text
```
 A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a "Principal" value represents every principal. Set the `*` to
make an instance of a service public through the Internet like this following rule.
```json
"Principal": {
"AWS": "*"
}
```
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
The `AdministratorAccess` policy looks like this
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Set a session token for the profile
```sh
aws configure --profile PROFILENAME set aws_session_token
A principal can have multiple policies attached.
Policies like `assume-role` and `switch-role` can lead to the gain of roles
with higher permissions
A `*` inside a "Principal" value represents every principal. Set the `*` to
make an instance of a service public through the Internet like this following rule.
```json
"Principal": {
"AWS": "*"
}
```
Administrator access policies can be queried to see who has elevated permissions.
```sh
aws iam get-policy --policy-arn arn:aws:iam::aws:policy/AdministratorAccess
aws iam get-policy-version --policy-arn arn:aws:iam::aws:policy/AdministratorAccess --version-id v1
```
The `AdministratorAccess` policy looks like this
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "*",
"Resource": "*"
}
]
}
```
### AWS Organizations
An organization is a tree structure, made out of a single root account and
Organizational Units (UOs). UOs can have children UOs. AN UO may contain
multiple AWS accounts. An AWS account can contain multiple user accounts.
An organization has IAM and SSO that also works with external identity
Providers (idP). This is done through the AWS IAM Identity Center which is used
to confiure roles and permissions.
Further, there is a management account inside any organization. It owns the
role "OrganizationAccountAccessRole". This account uses the policies/roles
mentioned in the [User Policies](#User-Policies) which are `assume-role` and
`switch-role` on the cli tool and the management web-console to gain
administrative permissions over the UOs inside the organization.
By default the Service Control Policy (SCP) `p-full-access` it attached to
every account inside the organization. This SCP allows subscription to all AWS
services. An account can have 5 SCPs at max. Limiting SCPs do not apply to the
management account itself.
### User Provisioning and Login
When using the cli command, the aws configuration and credentials are stored at `~/.aws`
[The
documentation](https://docs.aws.amazon.com/cli/latest/userguide/cli-authentication-user.html)
show how to setup the user login.
Add the credentials to the default plugin via
```sh
aws configure
```
Add credentials to a profile which is not default via
```sh
aws configure --profile PROFILENAME
```
Set a session token for the profile
```sh
aws configure --profile PROFILENAME set aws_session_token  Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity
Provider (idP) is connected to AWS SSO as a part of federated access. E.g. the
Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `
Users can be put into groups instead of direct role assignment, to specify
permissions for a collection of users.
```sh
aws iam list-groups
```
Roles can be assumed by other trusted users through policies. Assumed roles are
needed, so that aws support has access to some resources or external identity
Provider (idP) is connected to AWS SSO as a part of federated access. E.g. the
Role for support is `AWSServiceRoleForSupport`.
```sh
aws iam list-roles
```
Gaining access to important roles like maintenance opens the door to higher permissions.
Services use resources bound to the IAM inside the account. The scheme for
services is `