3.4 KiB
2025-07-20
Directory Writeup — TryHackMe
This blog post is a writeup of the Directory challenge on TryHackMe
What ports did the threat actor initially find open? Format: from lowest to highest, separated by a comma.
We can see that the attacker is scanning ports on the target system. If there
would be an open port on the target system, the answer would include SYN/ACK,
which is a flag of 0x12.
tshark -r ./traffic-1725627206938.pcap \
-T fields -Y tcp.flags == 0x12 \
-e tcp.srcport -e ip.dst_host \
| sort -n | uniq | sort -rn
The threat actor found four valid usernames, but only one username allowed the attacker to achieve a foothold on the server. What was the username? Format: Domain.TLD\username
After extracting all HTTP files, the result shows that there are some potential usernames to be crafted from the names of the people mentioned on the page, which the adversary could try to login.
Filtering for Kerberos packages, it is clearly visible that the attacker tried to bruteforce the usernames
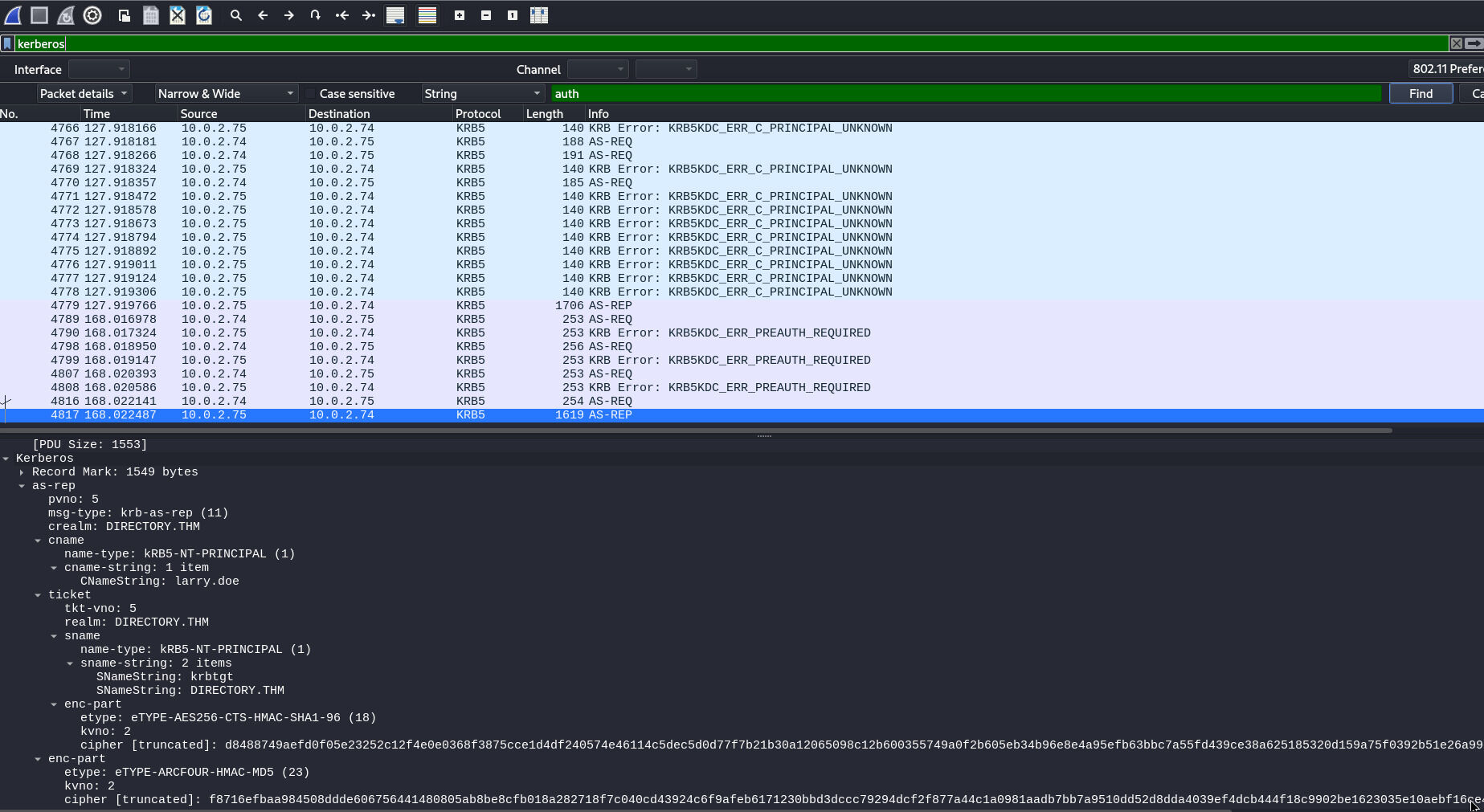
Only two requests did not end up in an error as a response. These contain the username we are looking for.
We need the CNameString as well as the SNameString in combination to get
the correct login name.
The threat actor captured a hash from the user in question 2. What are the last 30 characters of that hash?
The same AS-REP response package from the previous question contains an
encrypted part, which contains the hash as a cipher of type
eType-ARFOUR-HMAC-MD5 (23). This is the hash we are looking for.
What is the user's password?
We can use Krb5RoastParser to extract the AS-REP hash and crack it.
$krb5asrep$23$larry.doe@DIRECTORY.THM:f8716efbaa984508ddde606756441480$805ab8be8cfb018a282718f7c040cd43924c6f9afeb6171230bbd3dccc79294dcf2f877a44c1a0981aadb7bb7a9510dd52d8dda4039ef4dcb444f18c9902be1623035e10aebf16ce4bdf5f7064f480e67e96ec2eb32bad95c5a1247bd7a241273fe80e281f4e6a99926f7969fcf803190c7096b947a33407f8578d4c0fb8b52d2aa8d0405a44b72bd21e014563cb71e82aee0e12538d0d440c930b98abf766e18ddc99a964e6e812ecf8dc8994a912a02074d40e5e6906915c1d216653d45df88636b51656f2c37de2020a2fd86ee7ecf6f0afe3f509fd31144e1573f9587155616532b664cd0b50cda8d4ba469f
Use john or hashcat to decrypt the password.
john --wordlist=/usr/share/seclists/Passwords/Leaked-Databases/rockyou.txt ../kerb.hash
What were the second and third commands that the threat actor executed on the system? Format: command1,command2
There is a script to decrypt winrm traffic on jborean93's github page. Using the password we aquired before, the traffic can be decoded.
python winrm_decrypt.py ./traffic-1725627206938.pcap --password '********' > winrm.output
The parts we are interested in are the Powershell commands. We need to decode the commands, since these are b64 encoded.
grep "AAAAAA" winrm.output | cut -d '>' -f2 | cut -d '<' -f1 | base64 -d >> decoded.out
Now we can take e look at the commands using less or some other tool.
What is the flag?
We already decoded the commands in the previous step, just do a search for the flag structure in the already decoded output.
THM{***************}