2.7 KiB
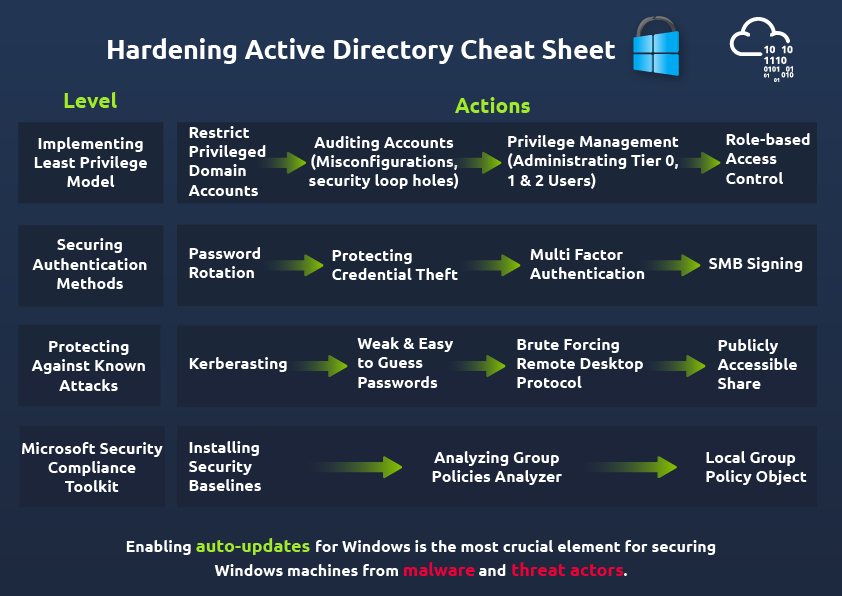
Active Directory Hardening
Policy Management Editor
Can be opened by right clicking on a domain in the Policy Management tool.
Do Not Store The LM Hash
LM hashes can be bruteforced, disable them under security options in the Windows settings of the group Policy Management Editor
Network Security: Do not store LAN Manager hash value on next password change
SMB Signing
Enable SMB signing in the Group Policy Mangement Editor under Security Options of the Local Policies of Windows Settings
Microsoft network server: Digitally sign communications (alway)
LDAP Signing
Enable LDAP signin in the Group Policy Mangement Editor under Security Options of the Local Policies of Windows Settings
Domain Controller: LDAP servers signing requirements
Passwords Policies
- Use Multi-factor authentication
- Use Group Managed Service Accounts (gMSAs) and rotate the passwords frequently
- Store a password history, so passwords won't be reused
- Set the password complexity through character pool and length of the password
- Use a passphrase
Set lifetime of passwords in the Group Policy Management Editor under Password Policy of Account Policies under Security Settings
Maximum password age
Least Privilege Model
Do not use administrational accounts for everyday work. Create accounts following these categories
- User accounts
- Privileged accounts
- Shared accounts
Role Based Access Control (RBAC)
Grant permissions through temporary roles. Do not use Discretionary Access Control (DAC) if possible.
Tiered Access Models (AD TAM)
Prevention of privileged credentials from crossing boundaries, either accidentally or intentionally. Similar to the ring model
- Tier 0, includes administrational domain accounts, Domain Controller and groups
- Tier 1, Domain apps and servers
- Tier 2, unprivileged user
Auditing Accounts
Frequent audits and continuous monitoring of the accounts and groups status and changes.
Security Compliance Toolkit (MSCT)
Manage and implement domain-level policies via pre-defined baseline policies.
Installing Security Baselines
Download the Tools and the 'Security Baseline.zip' and install the Powershell script.
Policy Analyzer
It is included on the same site as the other tools.
RDP
Do not expose RDP to the internet without additional security measures in place.
Publicly Accessible Share
Use Get-SmbOpenFile cmdlet to look out for unwanted shares