4.4 KiB
AWS S3 Enumeration
Regions
A list of services by region is maintained by AWS There are global and regional services.
Watch out for the global and regional Security Token Service (STS) which provides temporary access to third party identities, since regional STS are also valid in other regions. Global STS are only valid in default regions.
In aws cli, Regions go the cli argument --region
Simple Storage Service (S3)
S3 is an object storage without volume limits. The names of buckets are unique and the namespace of buckets is global but they are stored regionally.
Methods of access control are as follows
The aws cli scheme is
http://<bucketname>.s3.amazonaws.com/file.name
or
http://s3.amazonaws.com/BUCKETNAME/FILENAME.ext
- List content of public bucket via
aws s3 ls s3://<bucketname>/ --no-sign-request
Download via curl, wget or s3 cli via
aws s3 cp s3://<bucketname>/foo_public.xml . --no-sign-request
ACL
If the ACL is set to
Anyone, justcurlAuthenticatedUsers,s3cli with aws key
IAM
Permissions are granted directly through user accounts or indirectly through roles the user has joined.
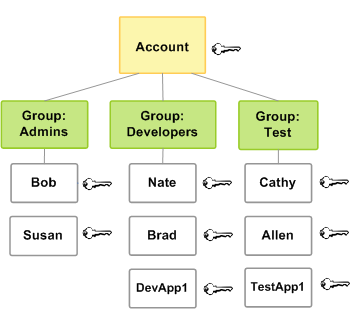
Gaining access to important roles like maintenance opens the door to higher permissions. An always unique AWS Account ID has a length of 12 digits.
The IAM is not necessarily used by S3. AK/SK is sufficient for authentication and authorization.
- Access key ID, starts with
AKIA+ 20 chars - Secret access key (SK)
- Session token,
ASIA+ sessionToken - AWS Organizations control accounts who joined
- Third party identity providers are supported
- IAM identity center of an organization allows provision of accounts from third parties through the AWS SSO
Root Accounts
Every AWS account has a single root account bound to an email address. This account has got the all privileges over the account. A root account has MFA disabled by default.
The account is susceptible to an attack if the mail address is accessible but MFA is not activated.
If the MFA is not set, it is an opportunity for a password reset attack when the account the vulnerable root belongs to is part of an AWS Organization.
User Policies
After authentication of a user (or principal) policies of the account are checked if the request is allowed. Policy evaluation can be found in the AWS docs. The following graph is taken from the documentation, it shows the evaluation logic inside an account
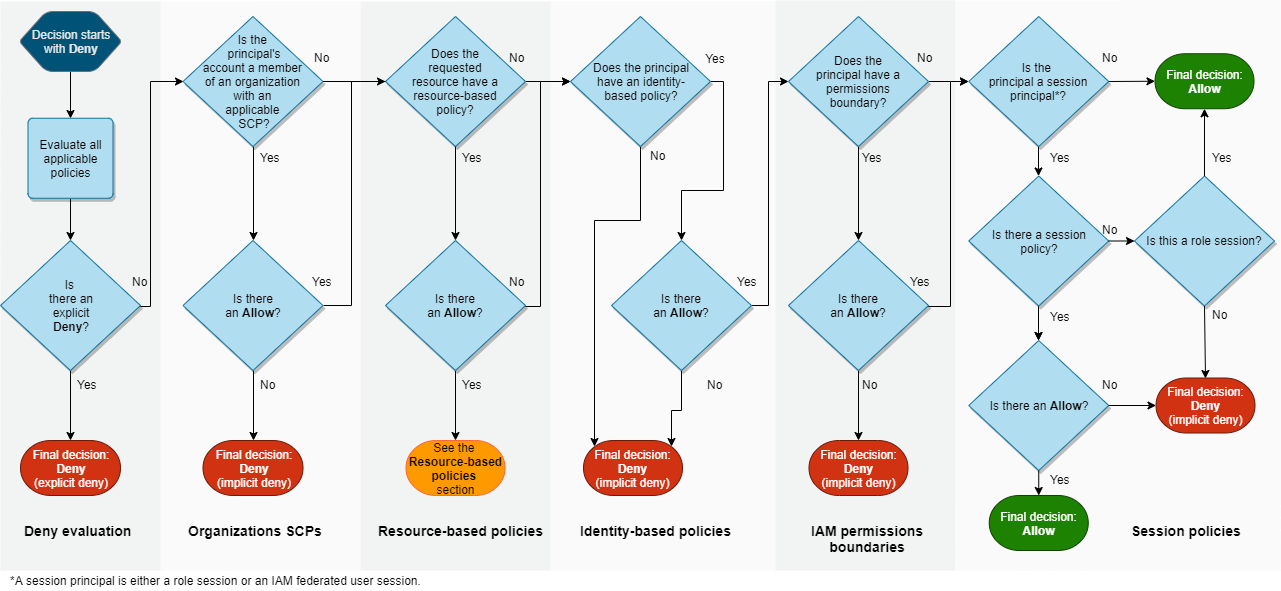
Policies like assume-role and switch-role can lead to the gain of roles
with higher permissions
User Provisioning
When using the cli command, the aws configuration and credentials are stored at ~/.aws
Add credentials to profile via
aws configure --profile PROFILENAME
Sanity test a profile through checking its existance via
aws s3 ls --profile PROFILENAME
Find account ID to an access key
aws sts get-access-key-info --access-key-id AKIAEXAMPLE
Find username to an access key
aws sts get-caller-identity --profile PROFILENAME
Listing EC2 instances of an account
aws ec2 describe-instances --output text --profile PROFILENAME
In another region
aws ec2 describe-instances --output text --region us-east-1 --profile PROFILENAME
AWS ARN
Unique ID is create through the following scheme
arn:aws:<service>:<region>:<account_id>:<resource_type>/<resource_name>
Secrets
aws secretsmanager help
aws secretsmanager list-secrets
ws secretsmanager get-secret-value --secret-id <Name> --region <region>
Check Permissions on S3 Bucket
Do a PUT method to see if the bucket may be writeable to upload a file via
curl -vvv -X PUT $BUCKET_URL --data "Test of write permissions"